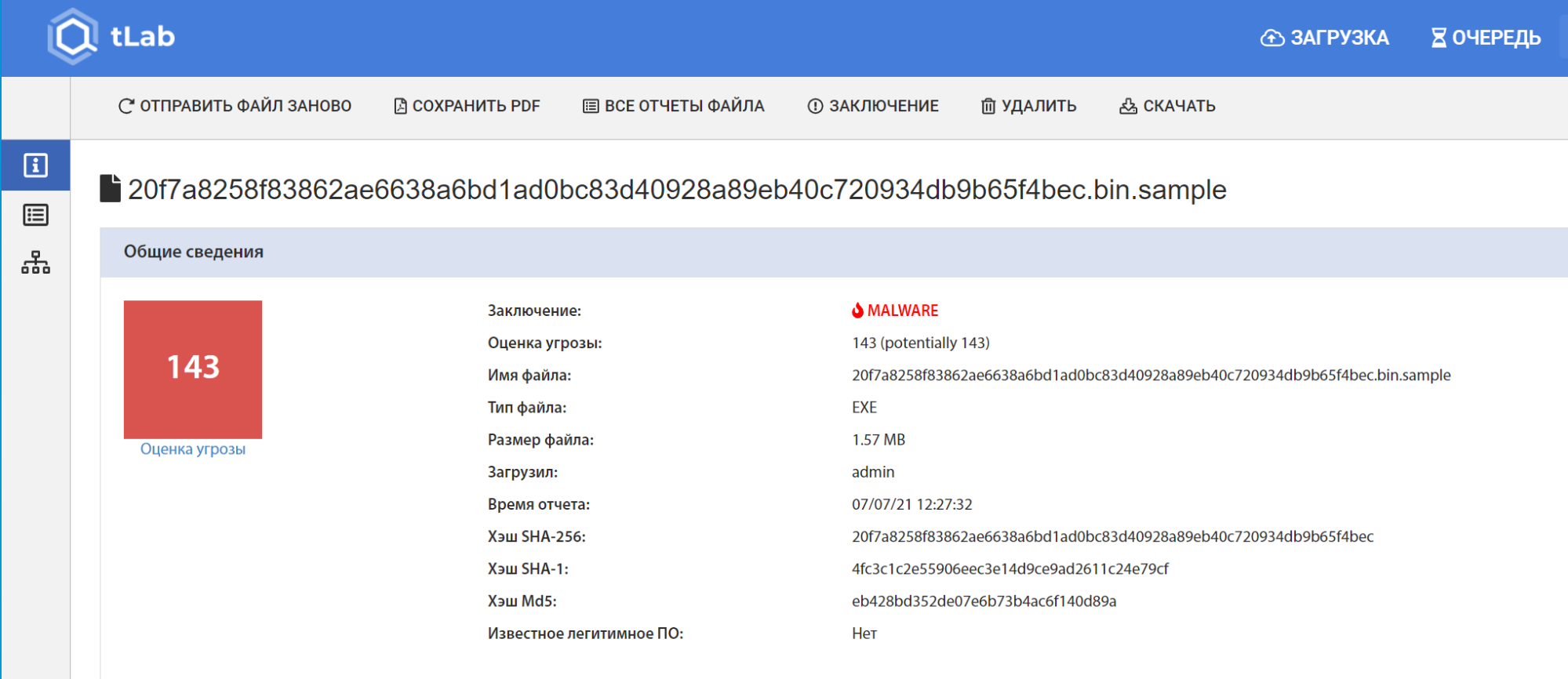
Watering hole” threat analysis in the government sector of Kazakhstan


While studying the threat landscape of Kazakhstan as a part of the Threat Intelligence phase, tLab Technologies experts discovered the so-called Razy malware family. The investigated samples of the Razy family apparently were used to infect users in the form of a Trojan downloader masquerading as a regular office document (Word, Excel and Adobe PDF). Attackers usually spread Razy using a “Watering hole” attack.
Thus the attacker achieves the trustworthiness effect since the link to the malicious file will likely be on a victim’s list of trusted sites.
Two of the analysed cases caught our sharp attention, in which the attackers spread the malware using the watering hole attack on the e-government portal (egov.kz).
Malicious links:
- hxxps://legalacts.egov.kz/application/downloadnpa?id=5322314
- hxxps://budget.egov.kz/budgetfile/file?fileId=1520392
At the same time, the second malicious Razy sample (at budget.egov.kz) was still available for download on the site at the time of detection.
The files are the same malicious Razy Trojan downloader. We assume that cybercriminals published the malicious software under the pretence of office documents by gaining access to uploading files to the legalacts.egov.kz and budget.egov.kz. The first document is a resolution of the district administration. The second, created in 2021, is a financial summary of the administration's budget. That implies the attacker posted the Razy malware in 2021, accordingly.
We assume that these attacks targeted specific companies that may be using these documents. And most likely, the attackers did not aim for the mass attack on the citizens of Kazakhstan, and the public exposure of the samples themselves is most likely a side effect. The rest of the Razy samples are also documents of different kinds, e.g. the resolution of the district administration. That means cybercriminals look for the documents suitable for the victim and embed them into the final malicious file.
One should note, by the time of publication, the malware control server (C&C server) has already been disabled, and that is currently, these samples cannot load any additional malicious functionality.
Together with the accountable employees of Zerde National Information & Communication Holding JSC, the tLab Technologies team worked to detect the Razy related incidents and block the caused spreading of malicious content.
tLab successfully detects and blocks this threat, which can be seen in the video below. tLab works on the principle of zero trust based on deep behavioral analysis, and high throughput allows you to analyze tens of thousands of files per day without filters and whitelisting, then our solution effectively blocks such threats even using an attack at the watering hole. Since tLab is used as part of the Cyber Shield of the Republic of Kazakhstan, we can say that the state is ready to repel such threats.
Samples technical analysis
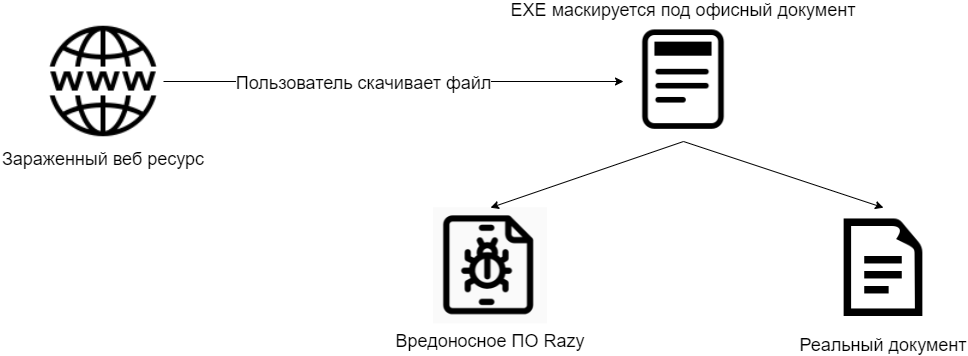
Razy, first spotted in 2015, has been used for attacks to these days. Below is a diagram of how Razy works. One can see that when a user launches a sample, a malicious payload gets activated, and an actual legitimate document embedded in malware pops up.
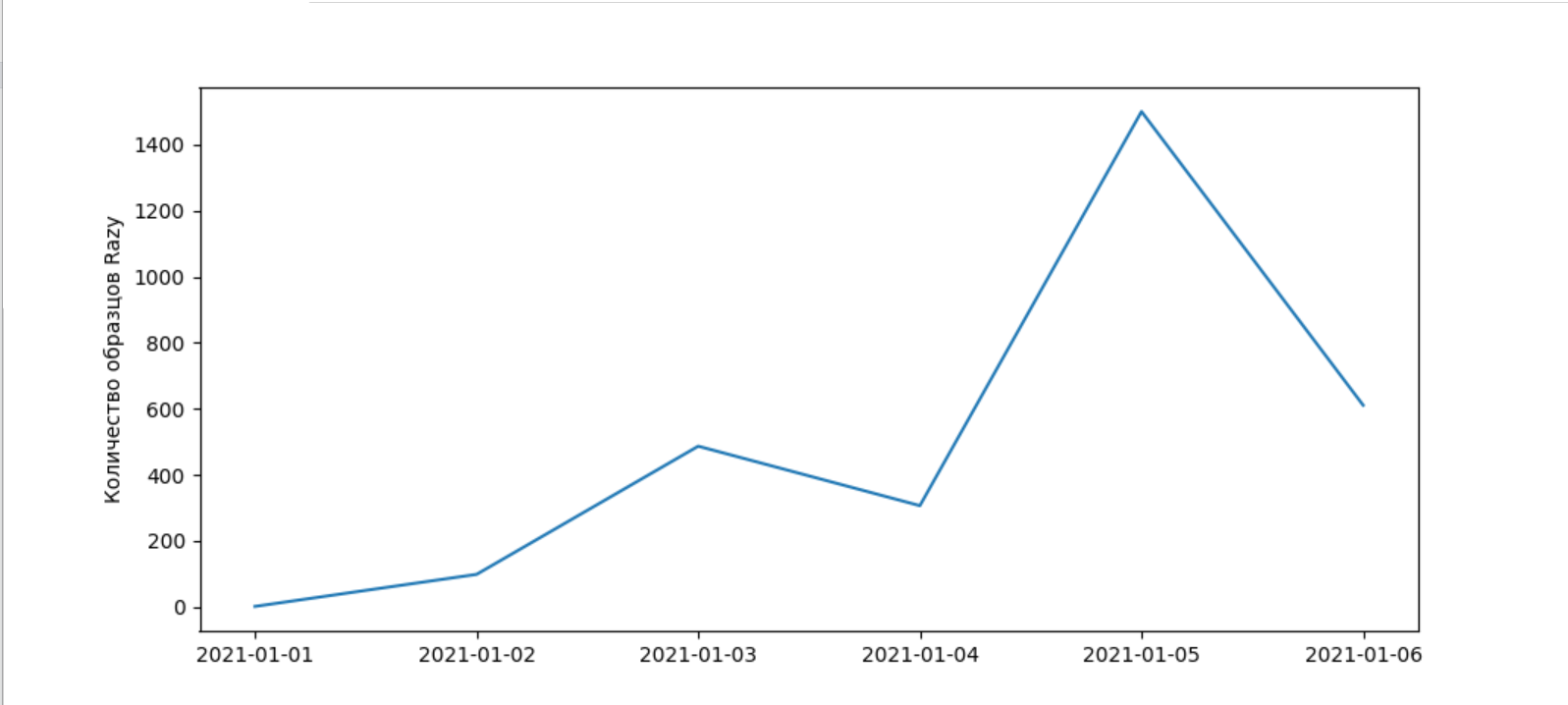
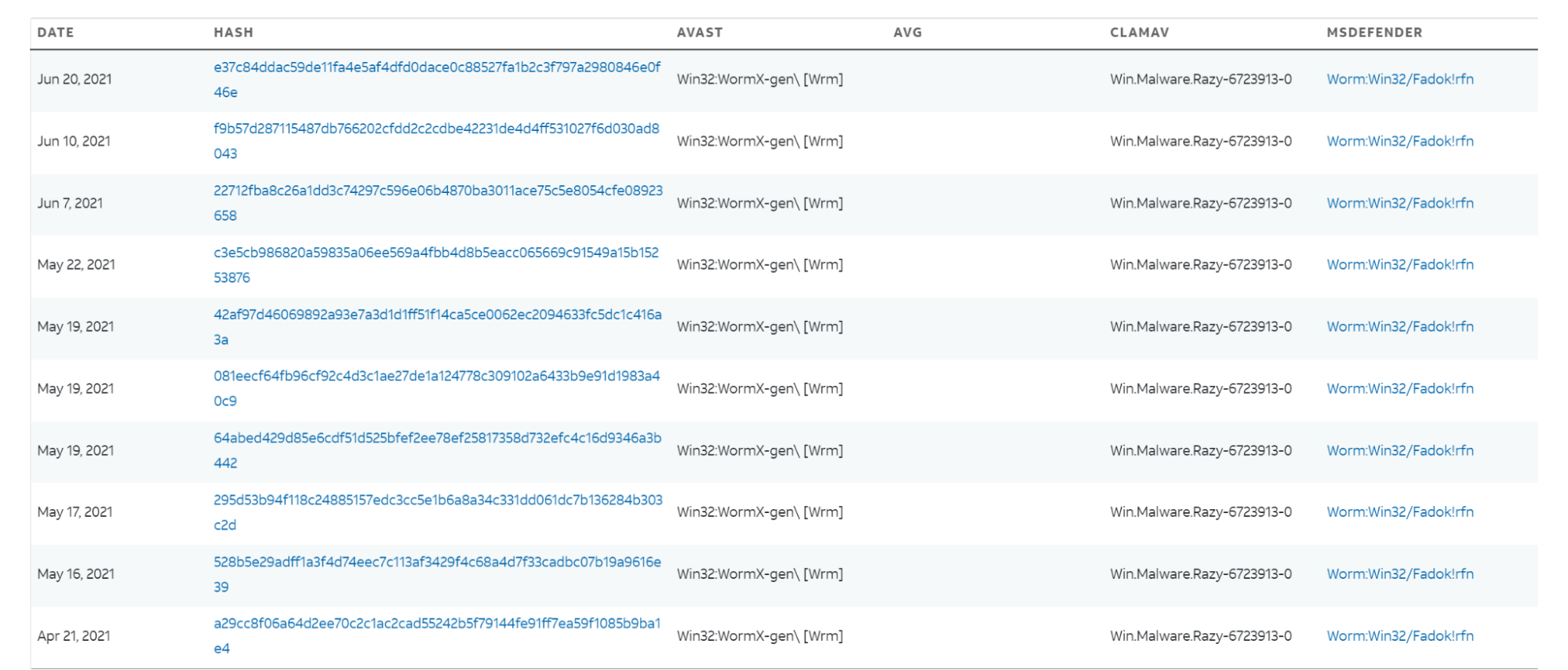
tLab Technologies monitored the monthly amounts of Razy malware samples found on Virustotal and discovered a sharp increase in May 2021. Most of the detected malware samples to target Kazakhstan belong to the same period. That is, the embedded documents come from the Kazakh institutions.
(2015 - 2019)
(2020)
(2021)
We researched the following files.
-
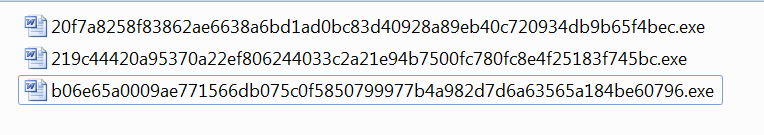
2 6>10 @CA.exeSHA256: 20f7a8258f83862ae6638a6bd1ad0bc83d40928a89eb40c720934db9b65f4bec
-
эльвира отчет.exeSHA256: b06e65a0009ae771566db075c0f5850799977b4a982d7d6a63565a184be60796
-
Отчёт по практике.exeSHA256: 219c44420a95370a22ef806244033c2a21e94b7500fc780fc8e4f25183f745bc
-
24160712_ExSteppeEagle_INTSUM_S2_160X_E_O.exeSHA256: 2F6C1C2C4043CA6D19ADDD60FA85A5AD6D347075E73AE1E1DCB76D5CC5224573
-
eastmere vil.exeSHA256: 7615E69D6FA11FC851C4CD10DDEE3820ACFC6170578C61AE74B6D4FD8EA71E10
-
OWNSITREP 241700AJUL16 G3.exeSHA256: 8FA473C03850B22C2C6AADCFE69268BE4E4C7A33881581FEA83789755AF8F22A
-
61c98d12-06b1-4f5d-9c12-ace5630dcc07SHA256: 3ED1B88C9AE34BA4FFBF8AED737F2DC9A0AEDEEDF8D2A4A69555518845E16264
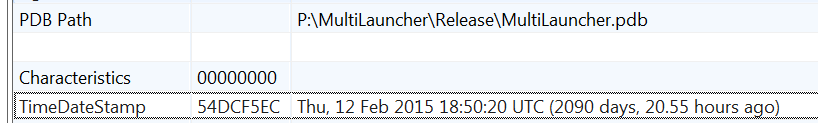
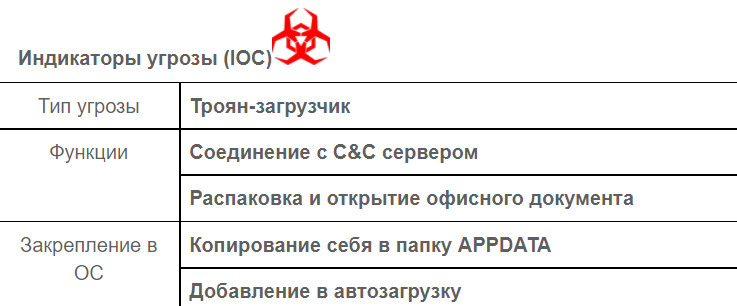
The identical PDB file paths and the timestamps found in all six samples indicate they were all created by a single “MultiLauncher” tool.
Most of the samples contain a document displayed to the user in resource number 200.
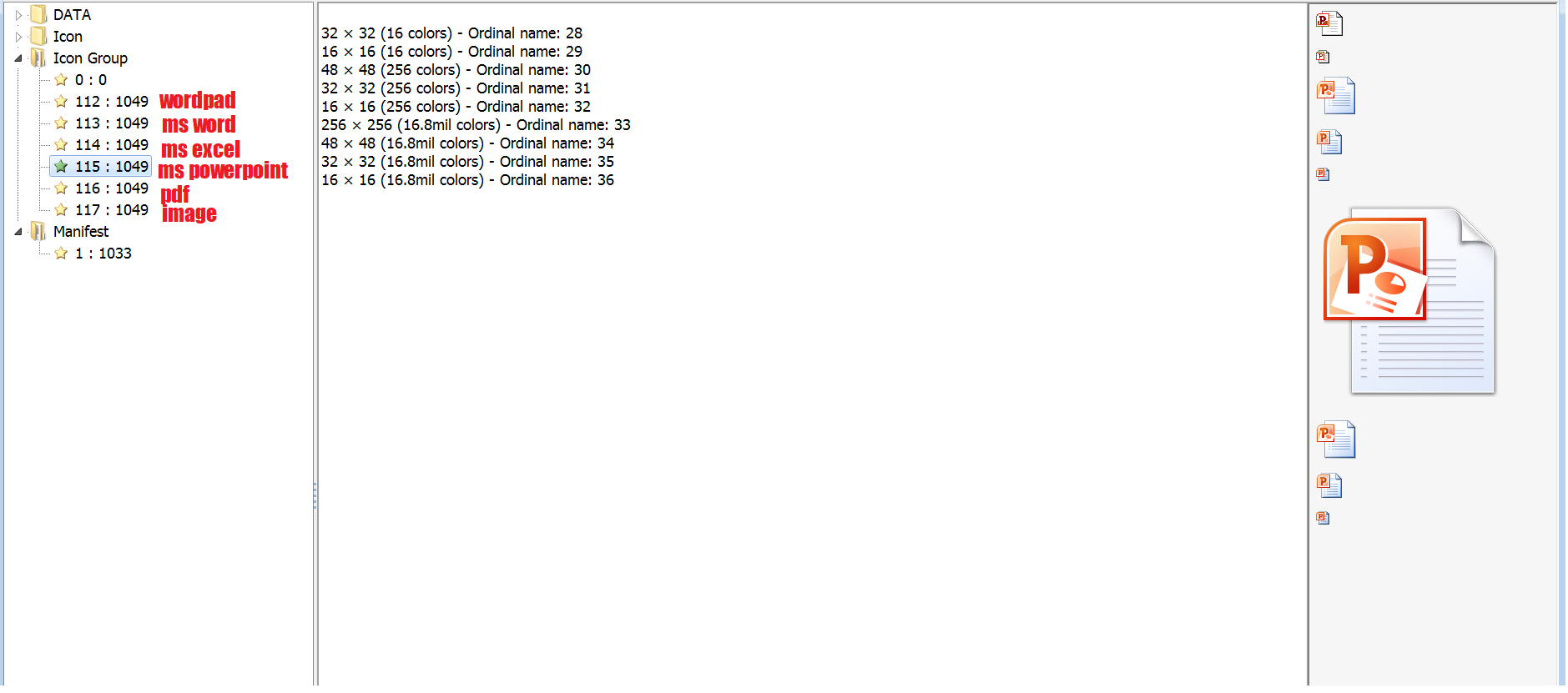
The samples contain icon sets for all types of documents. The final file uses one of the types. That leaves us with a conclusion the creators were using one tool and were choosing the required document type in the final build.
There are Razy builds that do not contain malicious documents:
- 1f35ce5d620f4eddbfbff5fd1b6142b002bb6a537b864d7745d96ddfd8424bd6
- 3a050db9c571eafd5b1dccb412991434bd0a0fc52c4771274018420a08af4c00
That explains that the attacker always looks for the “right” documents before embedding them into the final file.
The resource can be a PDF file also.
Usually, Razy is an EXE file with an office document icon.




All objects have the same functionality but different office documents. Since all of the samples are just variants of the same family, consider one of them.
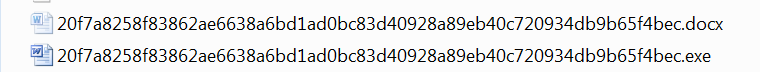
This object is an EXE file with an icon of a Word document. At a closer look, one can conclude, it is a dropper for office documents.
Launching the EXE file will result in a regular office document hiddenly located in the current folder.
The malicious file contains office document in its resources (DATA - 200):
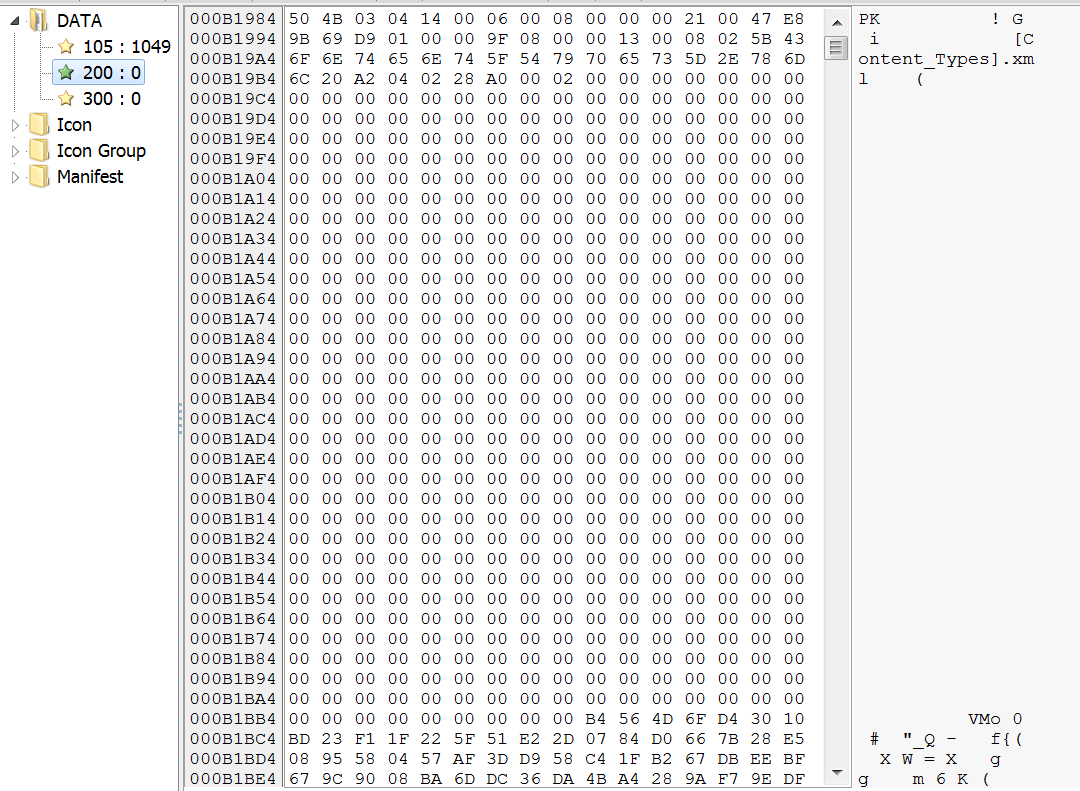
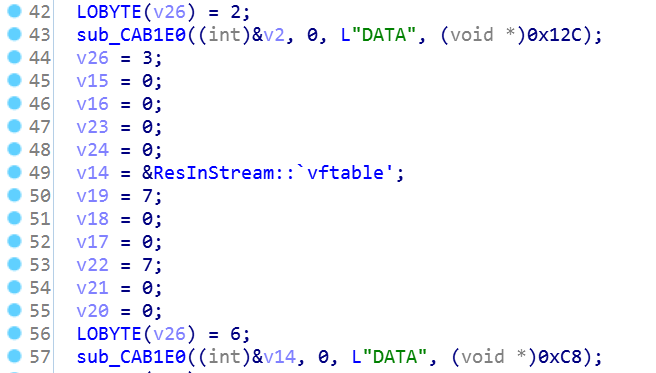
When launched, the Razy malware detects the type of displayed document given the information from the resource number 300 (0x12C):
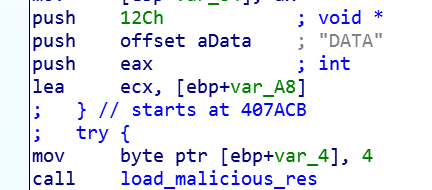
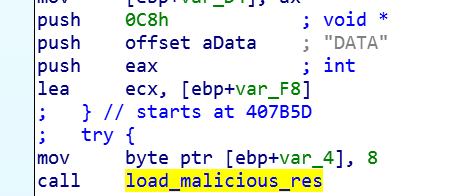
Next, the reading of the original office document from the resource number 200 (0x0C8) begins, using the FindResource, LoadResource, LockResource, SizeOfResource functions:

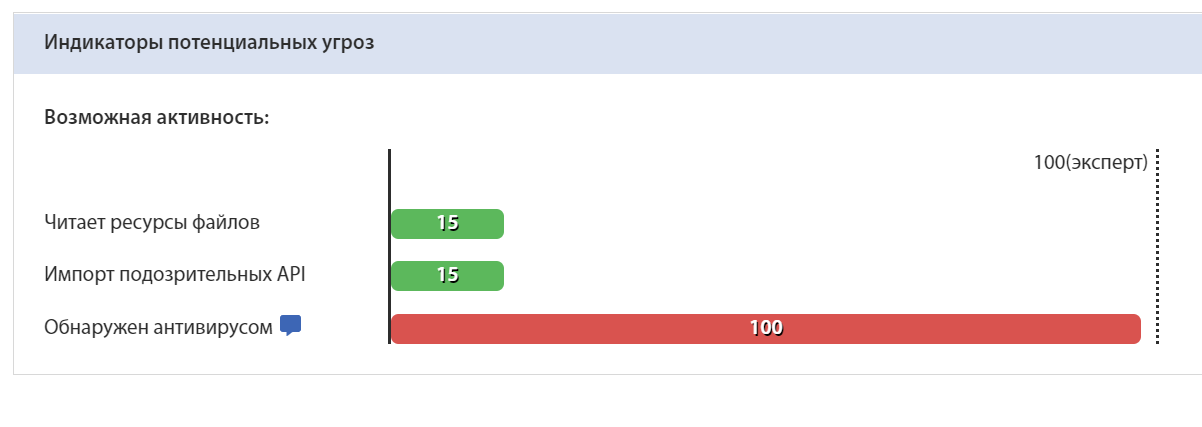
In the tLab sandbox, when uploading a file, one can see a potential threat indicator:
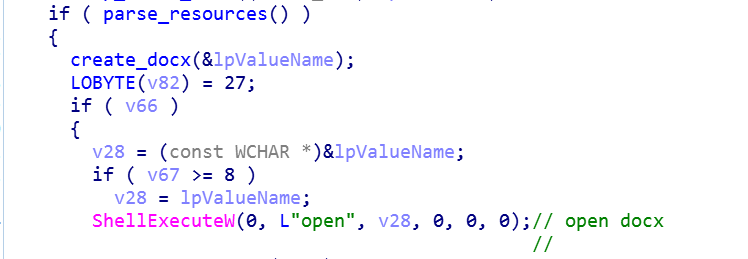
A malicious file opens a created document in Word using the ShellExecuteW function:
The tLab Technologies sandbox also builds a graph of the dynamic behaviour of an object:
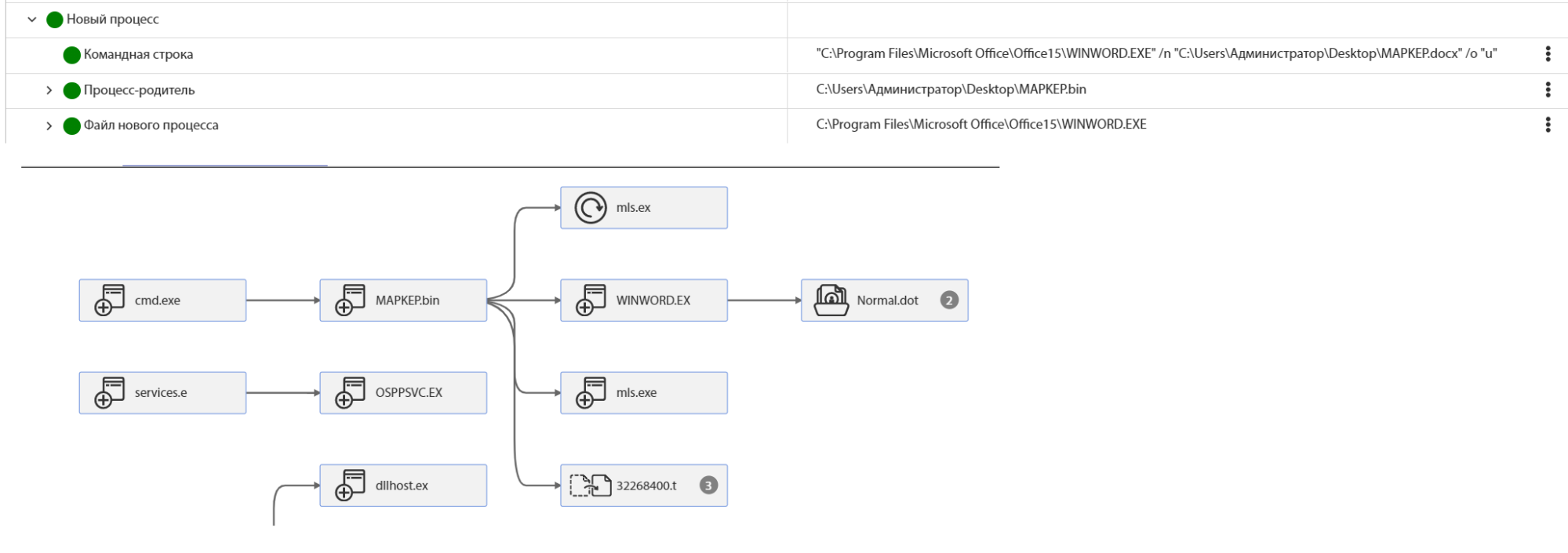
The Word document does not contain any macros and is not malicious, according to the initial analysis. Presumably, the purpose of opening an office document is to conceal malicious activity.
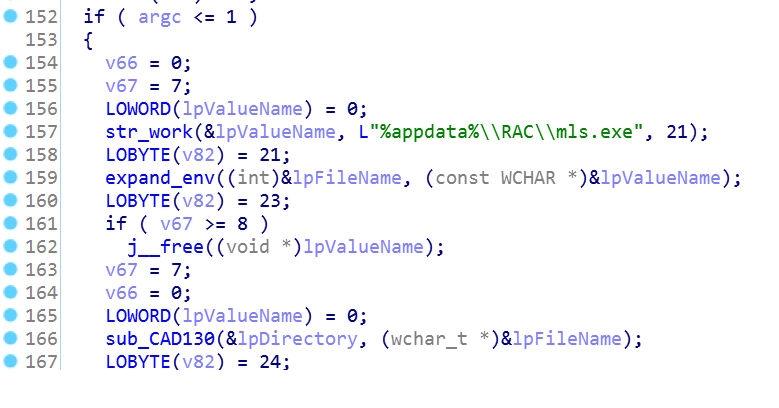
At the same time, the malicious file creates a copy of itself in the APPDATA \ RAC folder under the name mls.exe:
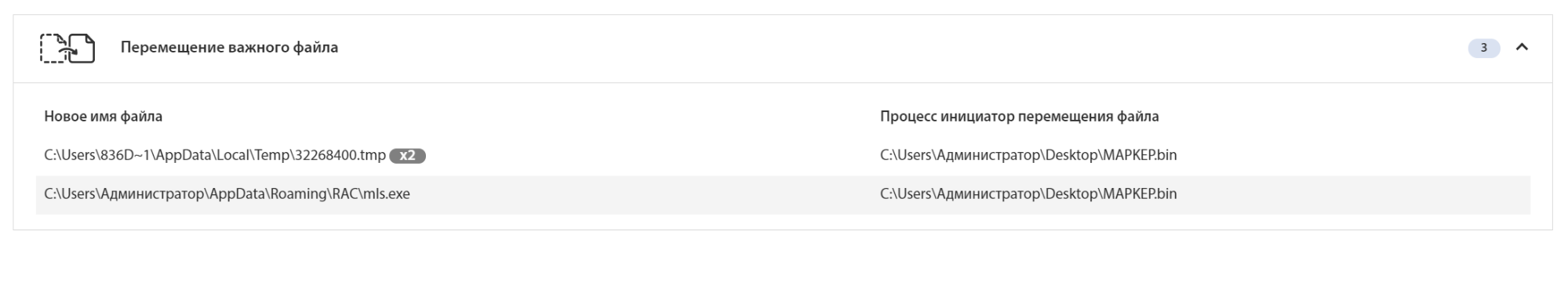
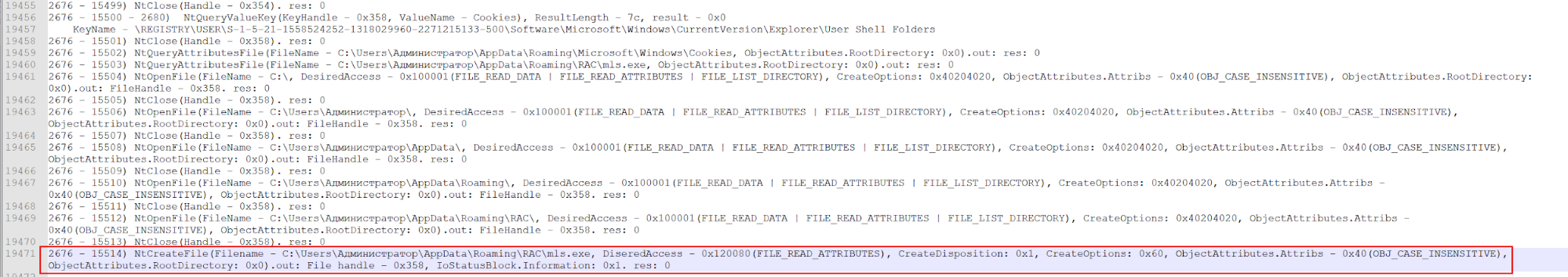
One can also observe this activity through the system call logs
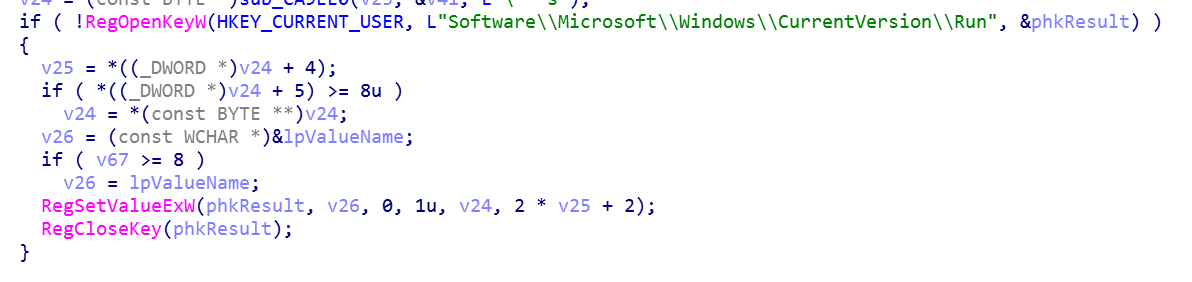
Next, mls.exe sets itself to startup in the registry with the -s parameter:
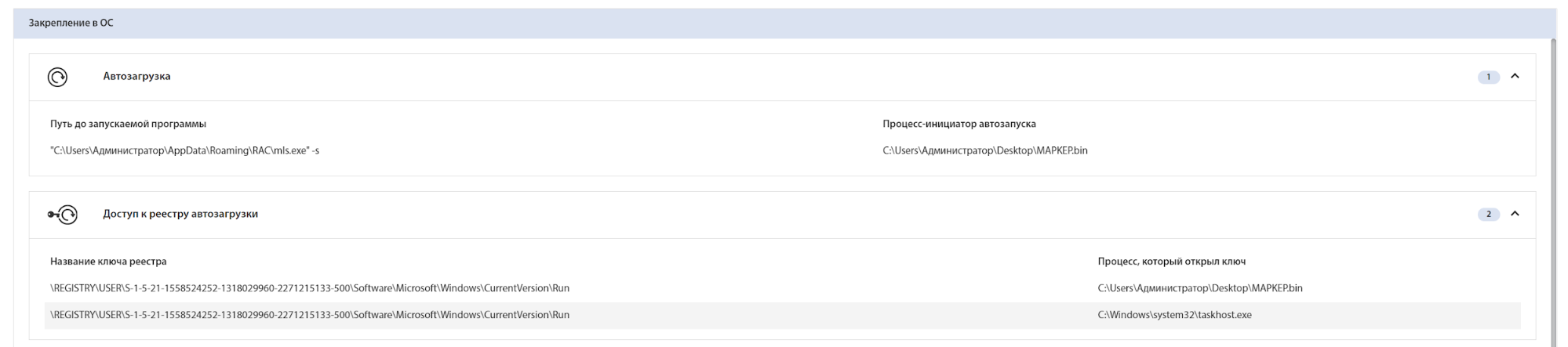
The file is present in the AutoStartup section of the tLab Technologies forensics tool
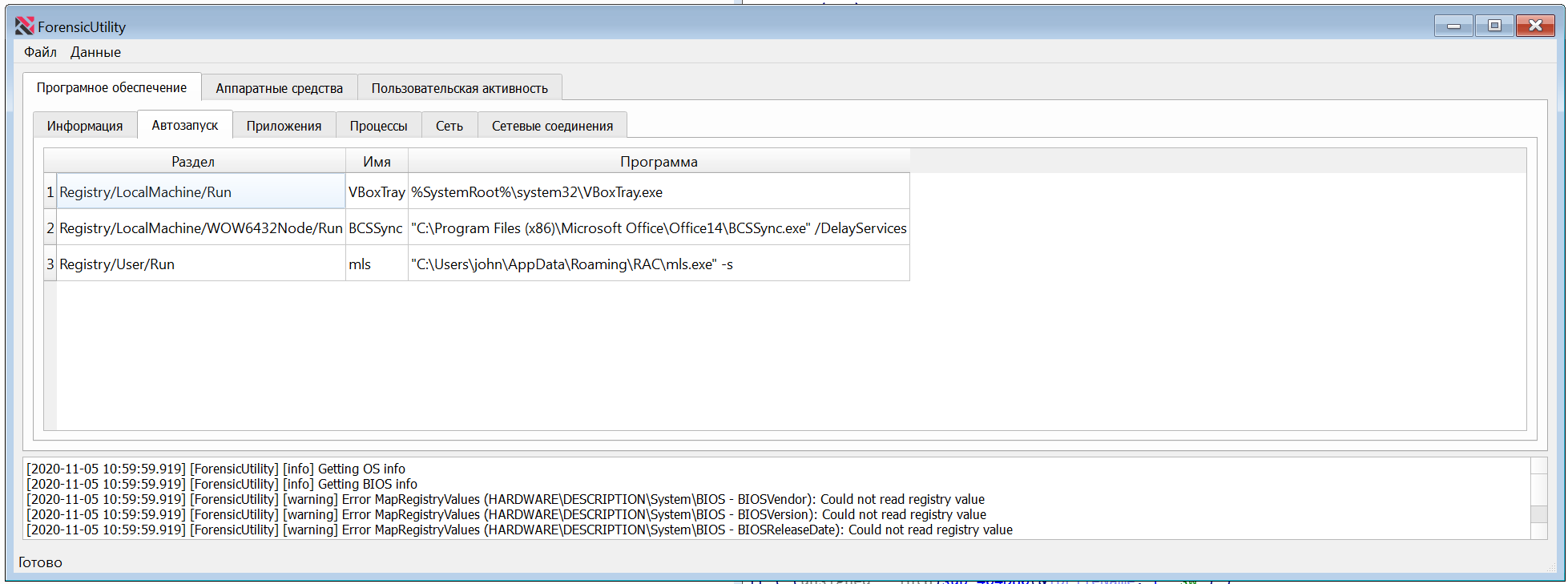
After rebooting, mls.exe will run with the -s option
After starting with the -s parameter, it calls the addresses hxxp: //wxanalytics.ru/net.exe.config and hxxp: //wxanalytics.ru/net.exe

The file can run with the -cs and -cc options. In this case, it takes the location path for the original malicious file.
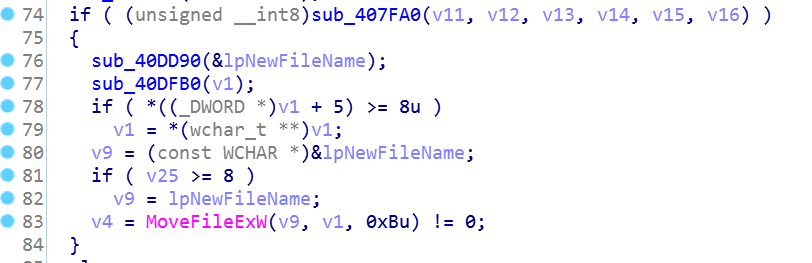
By looking at the list of malicious files that have accessed the same addresses, we will see they have different names.
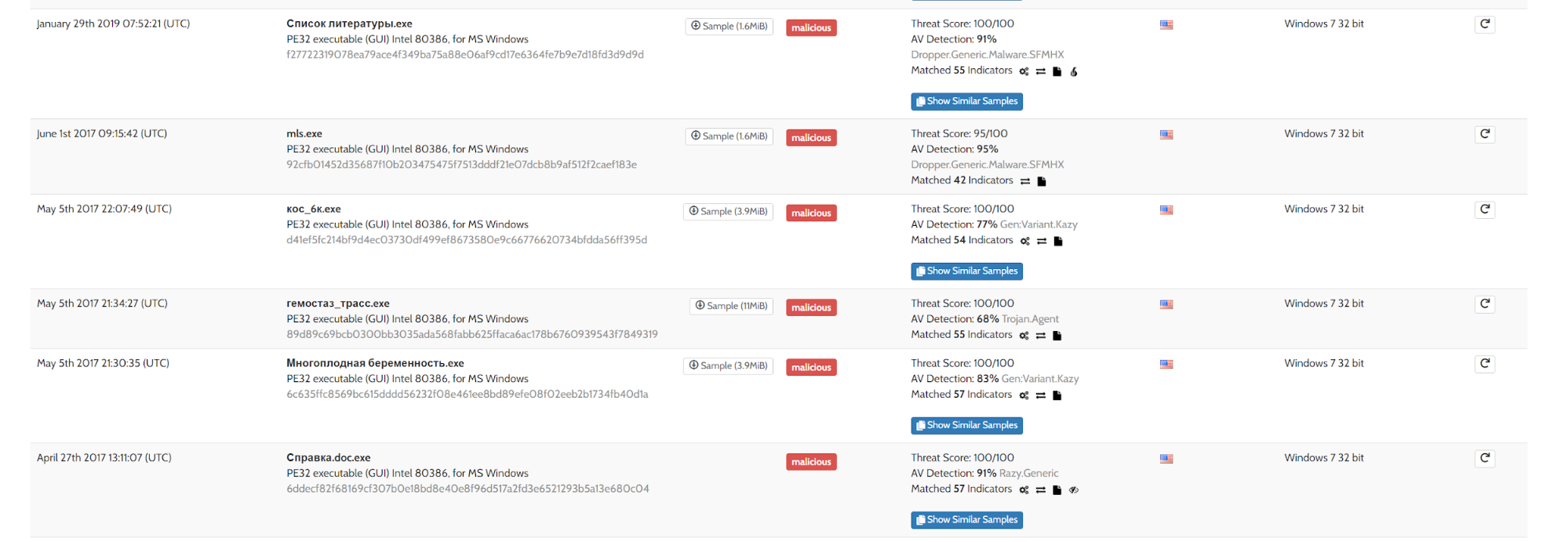
Several samples of malicious files on this list were uploaded documents to legalacts.egov.kz and budget.egov.kz. As previously noted, this type of attack is called a watering hole attack.
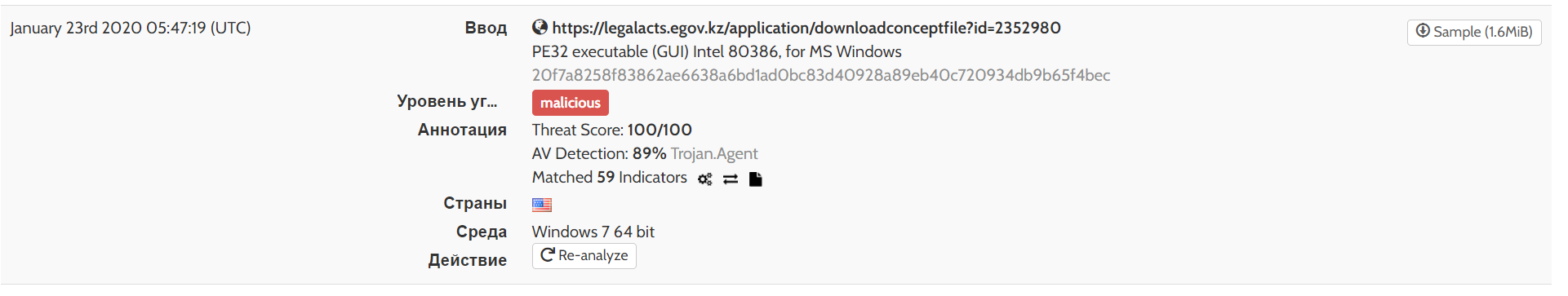
Malicious links:
- hxxps://budget.egov.kz/budgetfile/file?fileId=1520392
- hxxps://legalacts.egov.kz/application/downloadnpa?id=532231
The files are the same old malicious Razy downloader Trojan. We assume that cybercriminals published malicious software under the guise of DOCX by gaining access to uploading files to the legalacts.egov.kz site. As of May 11, 2021, only a few well-known anti-viruses identified the object, while none of them could detect the link to the object itself as malicious.
Conclusion
These days even an ordinary user can unravel such techniques as hiding files and faking the icons.
The malicious Trojan downloader itself is not packed in any way to stay undetected by the antivirus signature. The file creation date indicates the use of old-style malware. The hash sums of the studied samples (without resources) coincide with so many other files seen in similar attacks.
All this suggests that the attackers, in this case, used quite an old malware, changing only the office document displayed to the user, which indicates the low qualifications of the attacker. Regardless, the Razy Trojan still poses a live threat and uses actual white papers.
