Analysis of the WannaCry ransomware in the tLab system


In May 12, 2017 a mass attack by WannaCry virus-cryptographer aimed almost all versions of MS Windows took place. As a result of the attack more than 75,000 computers were infected around the world, including countries like UK, Spain, Germany, Russia. In addition officially computers in large companies in Kazakhstan were victims to the attack. The malware displays a message demanding a ransom of $300 to $600 (in Bitcoin cryptocurrency) for file decryption.
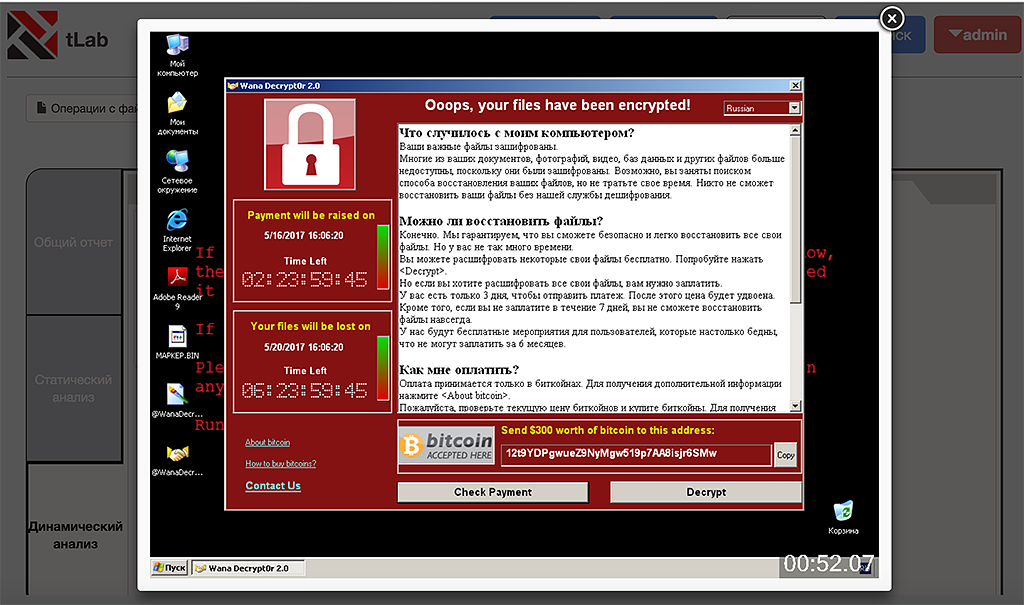 Ransom for file decryption (screenshot taken by tLab system)
Ransom for file decryption (screenshot taken by tLab system)
To distribute the cryptoworm attackers use a critical vulnerability MS17-010 in SMBv1 protocol. Although according to the official security bulletin this vulnerability is present in Windows versions starting from Vista, but the consequences of the attack were so severe that Microsoft has apparently decided to play it safe and took an unprecedented step - release a patch for Windows XP, which is no longer supported.
Specialists of the company T&T Security analyzed 2 objects related to this attack using tLab system.
Object 1
SHA256: 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
Object 2
SHA256: ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa
Dynamic object analysis in the system was carried out several times with various settings. The investigation was conducted in the containers without network connection, which is a typical configuration available to our customers. This article lists the most intriguing functionalities and features a comparative analysis.
tLab’s verdict
tLab system successfully identified both of the objects as malicious software by assigning a high threat level as a result of static and dynamic analyses.
tLab’s threat assessment is a numerical representation of the threat level in meta-percentage value (could exceed 100%), if more than the danger threshold (85% by default) - is considered malicious (highlighted in red). The threshold is set by the tLab administrator.
As a result, several indicators of potential threats were detected (functionalities) such as the persistence in the OS, atypical network activity, OS and user data modification and proxy activity. Considering it all, the first object demonstrated a 50% greater level of threat. This is due to the fact that this object has additional functionality, including the mechanism of self-distribution in a form of a network worm.
Almost all of dynamic analysis indicators pose a threat, exceeding 100 meta-percent. Mass activity indicator in particular stands out, exhibiting a huge number of repeating system events, which is anomalous for legitimate applications (in this case, iterating over thousands of IP-addresses from a possible range).
Taking into account the detected indicators our system automatically assigned an expert verdict - Dangerous.
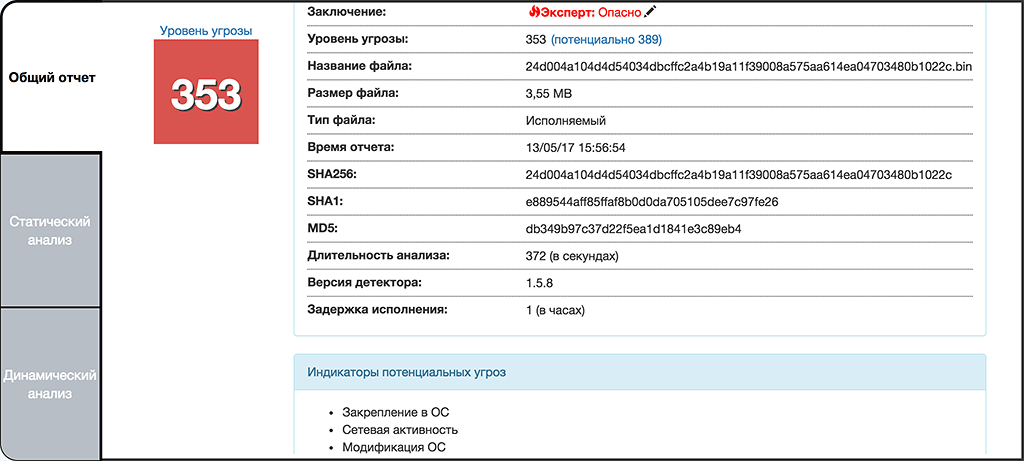 The object of study 1
The object of study 1
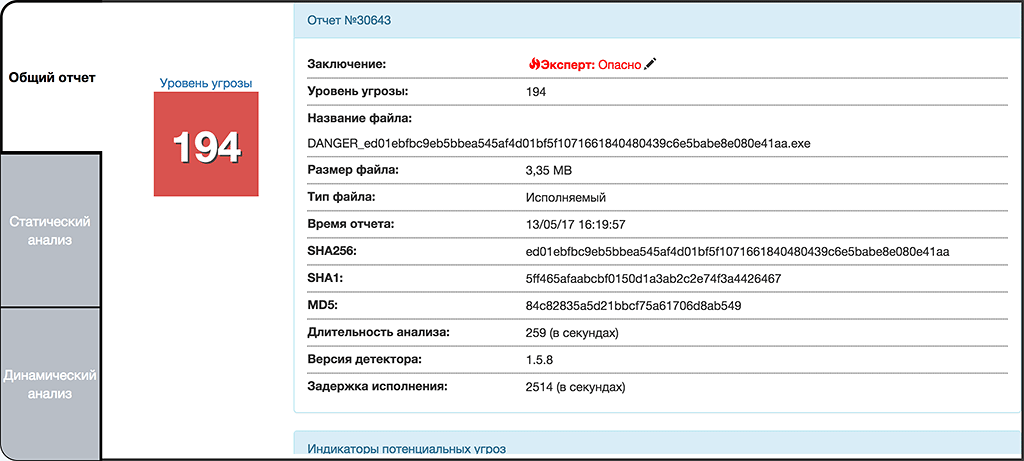 The object of study 2
The object of study 2
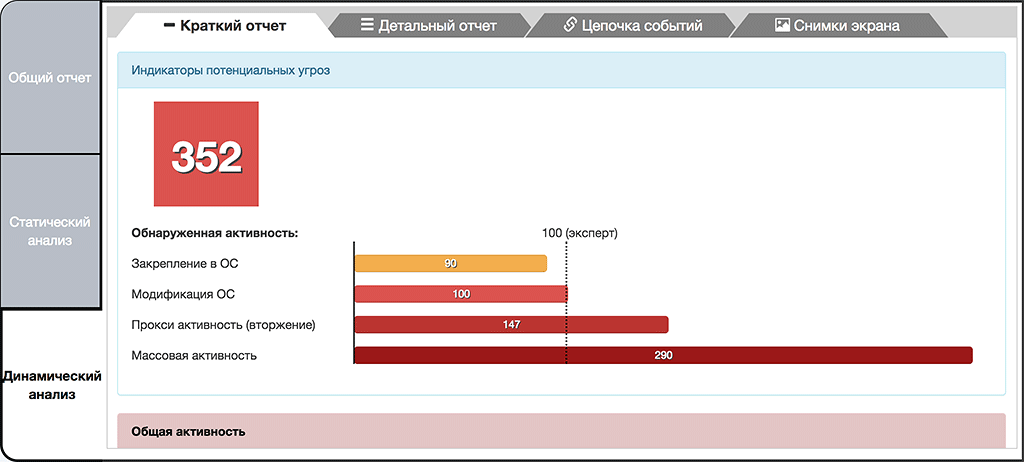 Report dynamic analysis of the object 1
Report dynamic analysis of the object 1
Payload
On a behavioral level both objects are similar and both encrypt user files, except that the first object has network worm functionality and attempts to spread via network vulnerability in SMBv1. To do this, it goes through many IP-addresses at random and attempts to connect to port 445 (SMB). Within 20 minutes of dynamic analysis in the sandbox, the malware managed to iterate over 60,000 IP-addresses from different ranges. Thus, the malware is able to spread itself not only on the local network of the victim, but also the ability to attack other computers on a global scale.
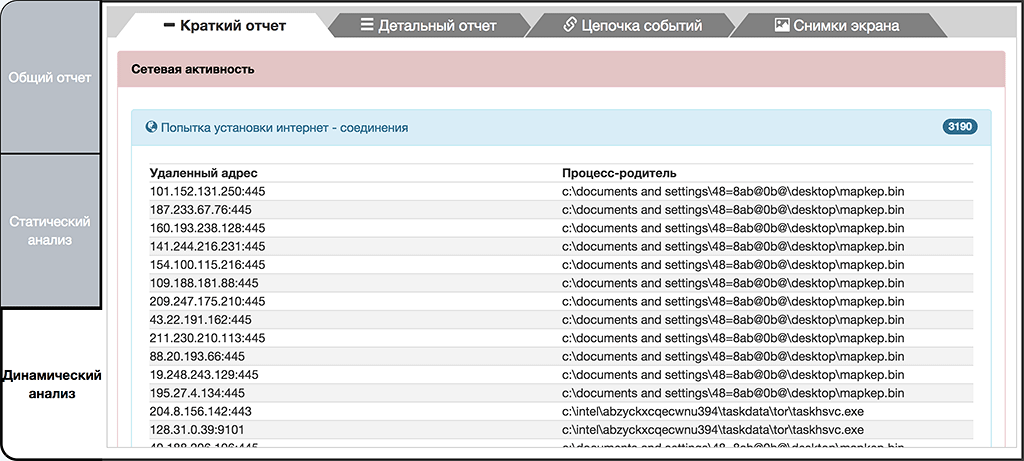 Enumerating IP-addresses for self-propagation (analysis 2 minutes)
Enumerating IP-addresses for self-propagation (analysis 2 minutes)
The extortionist servers issuing commands are located in the Tor network. During its operation, the malware connects to the ports 443, 9101, 9102 on the number of IP-addresses, which are the input nodes to the Tor network. In the process of yet another dynamic analysis tLab system detected connection attempts to the following addresses:
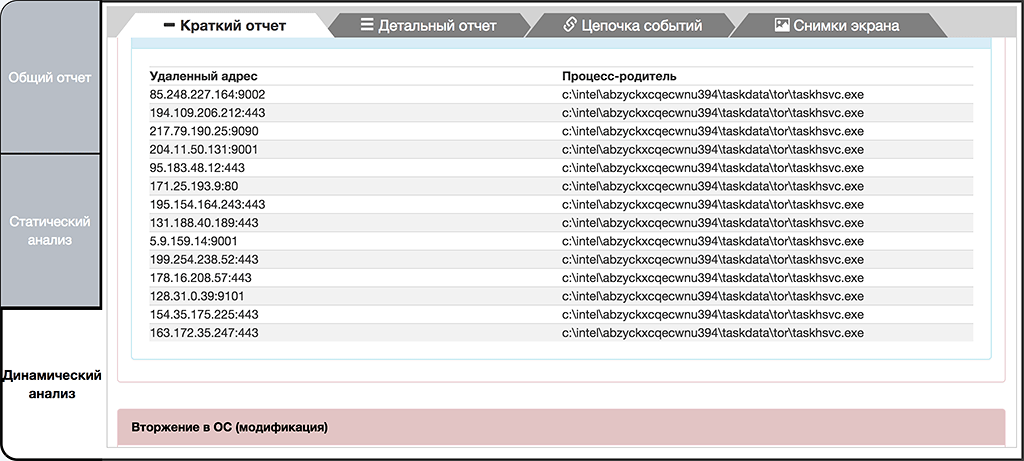 Attempts to connect to the Tor network
Attempts to connect to the Tor network
With every new dynamic analysis the given set of addresses varies, but it is always a Tor input node. Most likely, the sample randomly selects address:port combination from a predefined address list. At the time of writing, the number of Tor input nodes was more than 7000.
Installation and persistence in the operating system
Dynamic analysis showed that the objects are inserted in the operating system, either directly or through the extracted executable file "tasksche.exe", which is an installer for a group cipher components. As seen from the screenshots, the malware uses a legitimate system utility to add its own object to the autorun. Such an approach is classified as proxy activity which is typically used to bypass antivirus detection. In addition, the Object 1 further installs services to ensure the survival of its components. It is interesting to note that this malware initially installs itself as a service and all the activity in the future is done by that service.
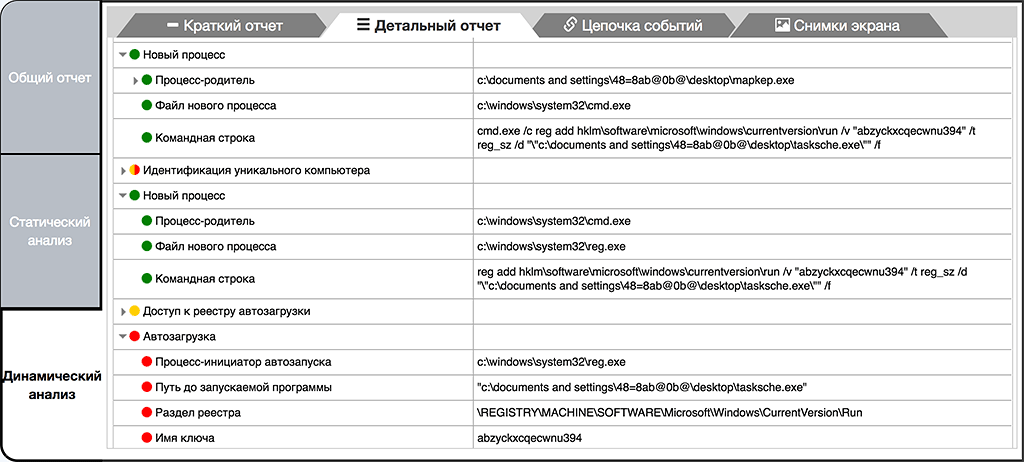 Creating objects 2 registry key using a proxy activity through the system utility reg.exe
Creating objects 2 registry key using a proxy activity through the system utility reg.exe
It is interesting to note that this malware initially installs itself as a service and all the activity in the future is done by that service.
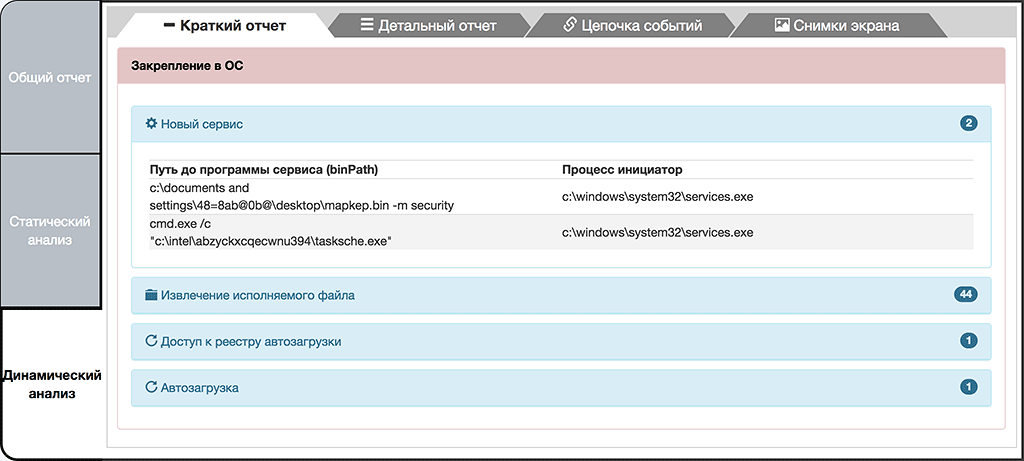 Creating a service object 1
Creating a service object 1
During the installation process "tasksche.exe" or the malware extracts from itself and runs the file "@wanadecryptor@.exe" many times into a variety of user folders and other directories containing files of interest, presumably in order to avoid a single point of failure or discovery.
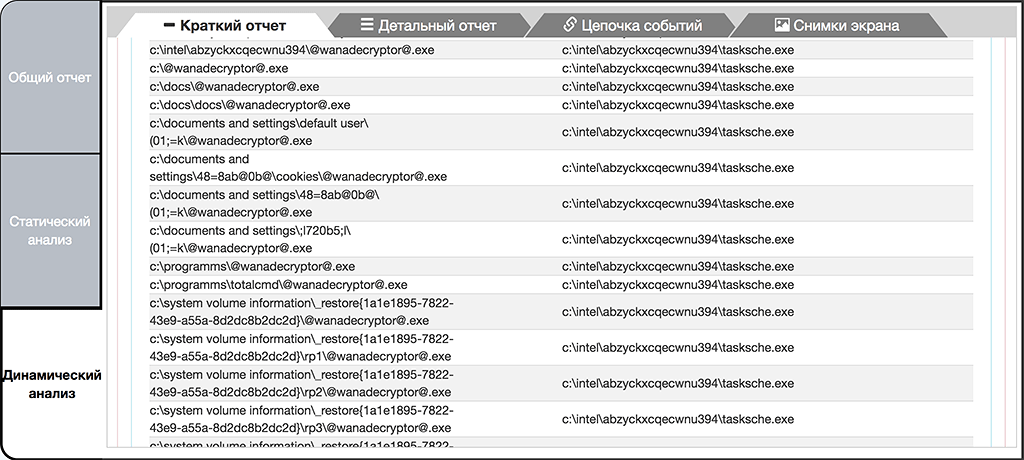 Extraction of "@wanadecryptor@.exe" into different directories
Extraction of "@wanadecryptor@.exe" into different directories
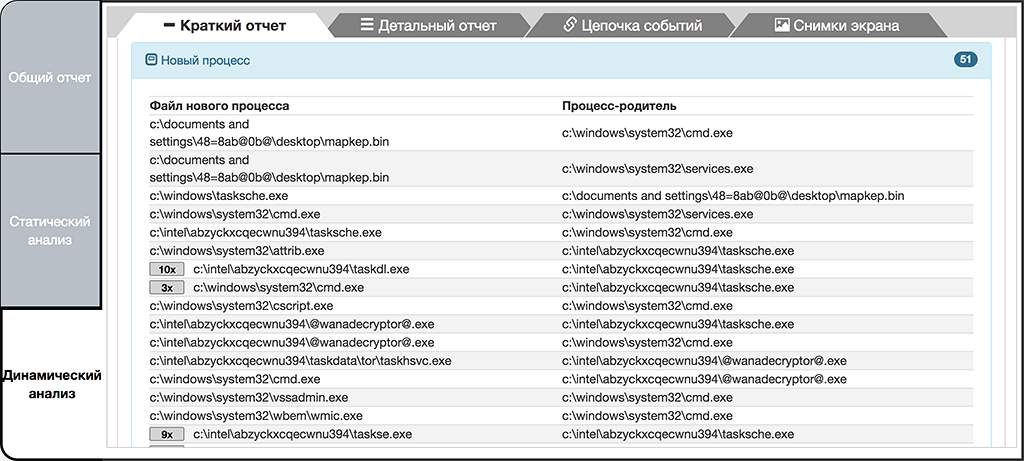 Running the extracted components
Running the extracted components
The process of "@wanadecryptor@.exe", in turn, retrieves the Tor-client components and launches its application "c:\intel\abzyckxcqecwnu394\taskdata\tor\taskhsvc.exe".
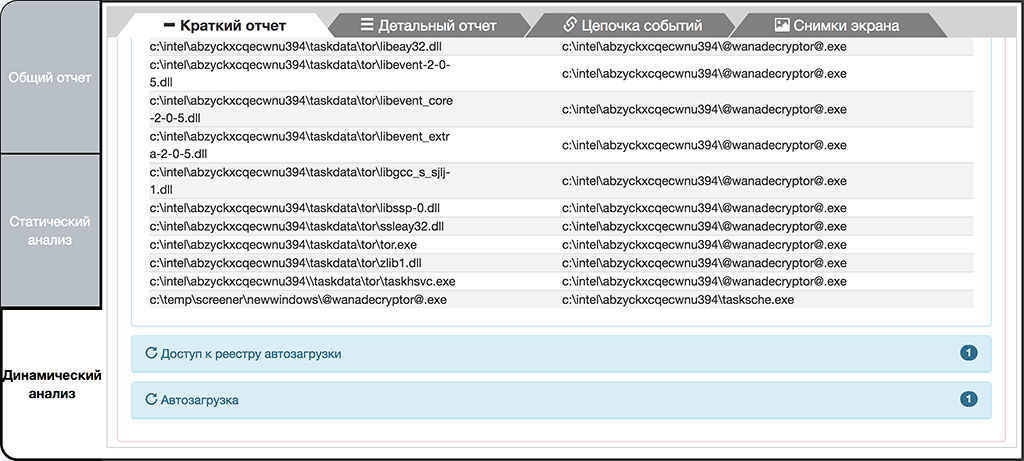 Extraction of the dependency cypher
Extraction of the dependency cypher
In addition, this process makes a number of system operations using Windows commands, namely, disables Shadow Copy support, deletes existing copies, and disables means of recovery that by default launch during boot-up process.
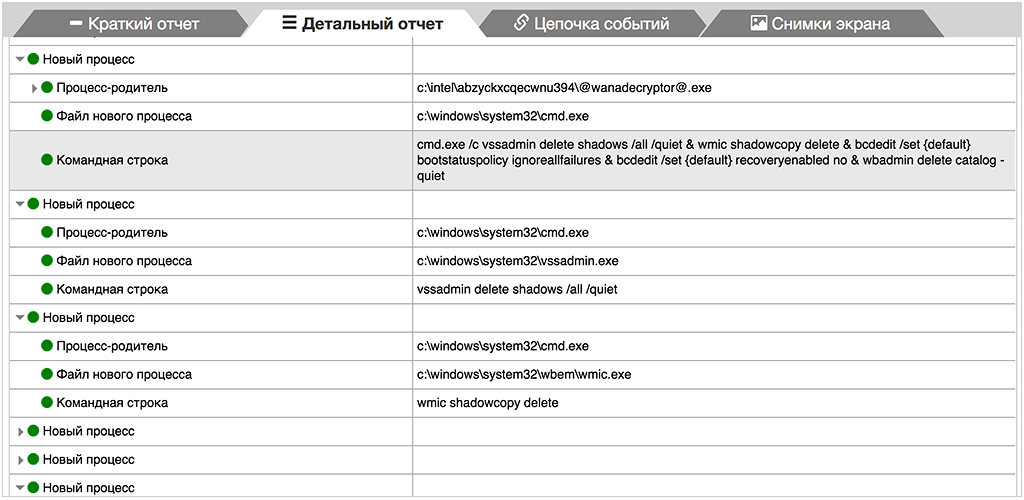 System command (highlighted attribute)
System command (highlighted attribute)
Malware features
According to the analysis, this malware has a complicated activity structure which manifests itself in the usage of multiple independent components, objection reservations and methods of proxy activity. As can be seen from the chain of activity produced by tLab system, the initial malware extracts a number of objects and through which it installs itself unto the system (autorun), iterates through Tor network input nodes, modifies OS configuration and runs encryption components on user files. The more detailed chain of activity demonstrates multiple launches of extracted encryption components, which in turn was identified by tLab system as an abnormal mass activity with a high threat level.
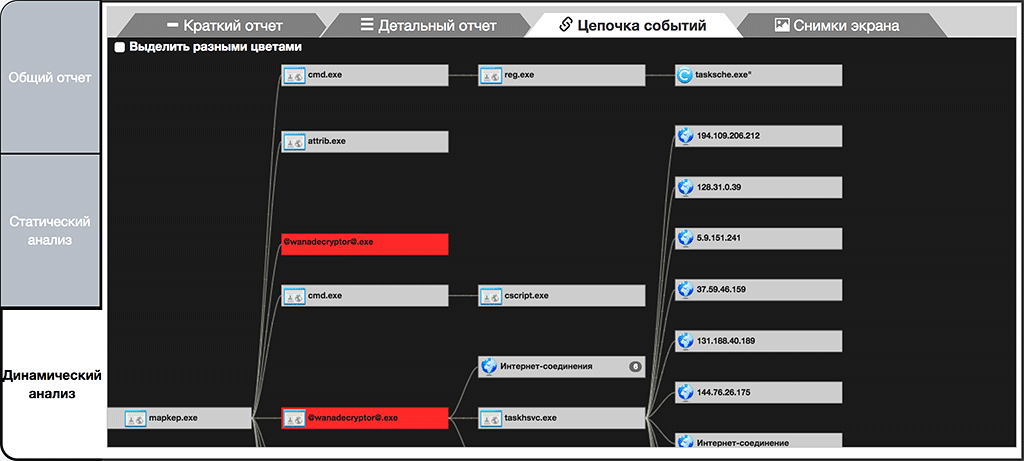 In addition, this process makes a number of system operations using Windows commands, namely, disables Shadow Copy support, deletes existing copies, and disables means of recovery that by default launch during boot-up process.
In addition, this process makes a number of system operations using Windows commands, namely, disables Shadow Copy support, deletes existing copies, and disables means of recovery that by default launch during boot-up process.
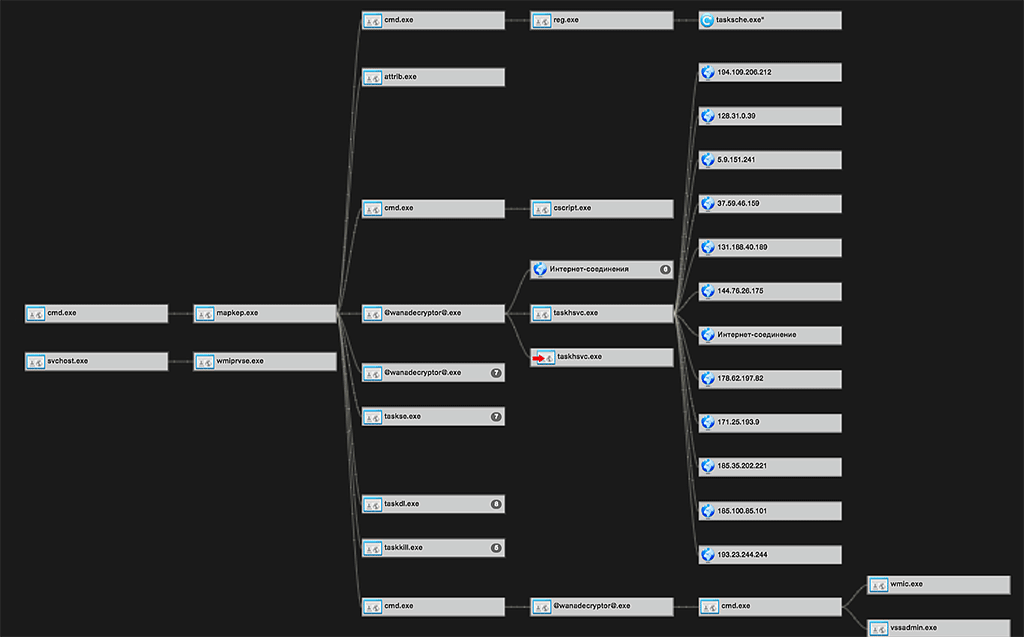 Aggregate chain activity object 2
Aggregate chain activity object 2
Among all of its embedded functionality the malware does not possess means to hide its presence. Attempt to do so or to identify the runtime environment today are classified as critical IoC (Indicator of Compromise, threat indicator). As such, we are seeing a trend where malware try not to stand out from the general flow of such programs of legitimate activity as installers, archiver, file managers. However, even with this approach to malware development, tLab system is able to recognize the threat, thanks to our deep behavioral analysis technology.
